In recent years, blockchain technology and Blockchain Security companies have gained popularity as safe and decentralized methods of data storage and transfer. A blockchain is fundamentally a distributed digital ledger that is accessible through a network of computers. The chain’s blocks each include a number of transactions, and once a block has been included in the chain, its contents cannot be changed or removed. Blockchain systems are very safe due to their decentralized organization and usage of encryption methods.
The resistance to attacks on blockchain technology is one of its primary security aspects. The most frequent attack on a blockchain system is known as a 51% attack, in which a number of bad actors gain control of more than half of the network’s processing capacity and use it to influence the system. However, due to the decentralized structure of blockchain networks, it is challenging for one organization to obtain this kind of dominance. In addition, a lot of blockchain-based systems use consensus techniques like Proof of Work or Proof of Stake to guarantee that the network is safe even from attacks.
The Sybil attack, in which a bad actor generates many identities to influence the network, is another sort of assault on blockchain systems. Many blockchain systems utilize digital signatures to prevent this, which let users validate their identities without disclosing personal information.
Another potential problem with digital currencies is double-spending, which occurs when one digital token is used more than once. Blockchain systems make a guarantee that every transaction is distinct and impossible to replicate using cryptographic methods like hashing.
Another crucial element of blockchain security is decentralization. The ledger is spread across a network of computers, eliminating any single point of failure that an attacker could exploit. Additionally, this makes it challenging for any one individual to influence the system.
Another aspect of blockchain technology that can improve security is smart contracts. The conditions of the agreement are directly written in the code for these self-executing contracts. They can be used to automate transaction execution and lessen the need for middlemen, which can improve security and transparency.
Blockchain technology is particularly applicable to business and industrial use cases where sensitive data may be protected via private and permissioned blockchain networks. More control over who has access to the data is possible thanks to these networks, which can also be utilized to meet legal requirements.
Blockchain technology has numerous advantages in terms of security, but it also has significant drawbacks. Scalability is a problem since, as of now, a blockchain network can only handle a finite amount of transactions. Since governments all over the world are still striving to create regulations for the use of blockchain technology, regulatory compliance is also a challenge.
Blockchain security is likely to keep developing in the future. To defend against anticipated attacks from quantum computers, which will be able to decrypt many of the present encryption techniques, quantum-resistant algorithms are being created. Additionally, the Internet of Things and other cutting-edge technologies are being connected with blockchain technology to create new opportunities for safe data transit and storage.
Types of attacks on blockchain systems, including 51% attacks, Sybil attacks, and double spending
Because it can offer a safe and decentralized method for data storage and transfer, blockchain technology has recently attracted a lot of attention. There are still security issues that must be resolved, like with any new technology. We’ll talk about some of the most typical attacks against blockchain systems in this post, along with the defenses put in place to thwart them.
The 51% attack is one of the biggest dangers facing blockchain networks. When a group of miners or nodes controls more than 50% of the computational power on a blockchain network, an assault of this type takes place. They can manipulate the network with this level of power by reversing transactions and double-spending. Blockchain networks must have a vast and decentralized network of nodes in order to prevent this kind of attack.
The Sybil attack is another style of assault against blockchain-based systems. This kind of assault happens when a bad actor on a network generates numerous identities or nodes in an effort to take over that network. Using a consensus mechanism like Proof of Work or Proof of Stake, which needs nodes to demonstrate both their identity and processing capability, can stop this from happening.
Another attack that can happen to blockchain systems is double-spending. When a bad actor has the ability to use the same digital assets repeatedly, this happens. Most blockchain systems use a method called unspent transaction output (UTXO) to ensure that each digital asset can only be used once in order to avoid this.
Hashing and digital signatures are two cryptographic methods that are used to protect blockchain transactions. Digital signatures are used to verify the identity of the individual performing the transaction, while hashing is used to establish a distinctive fingerprint of each transaction.
Another critical component of blockchain security is decentralization. Decentralized networks make it more difficult for attackers to take over the network since there is no single point of failure.
Another critical component of blockchain security is smart contracts. The conditions of the agreement are directly written in the code for these self-executing contracts. The automatic enforcement of the contract terms enables more safe and more efficient transactions.
In business and industrial settings, private and permissioned blockchain networks are also gaining popularity. These networks enable greater control over who has access to and can use the network, which can help to thwart assaults and guarantee regulatory compliance.
Blockchain security still faces difficulties, though. One of the main obstacles is scalability because existing blockchain systems can only process a certain amount of transactions per second. Governments all around the world are still finding out how to handle blockchain technology, thus regulatory compliance is also a worry.
As new tools and methods are created, blockchain security will keep developing in the future. To defend against assaults based on quantum computing, quantum-resistant algorithms are being created. Additionally, blockchain will probably be combined with other cutting-edge technologies like artificial intelligence and the Internet of Things.
The role of consensus mechanisms in securing blockchain networks, such as Proof of Work and Proof of Stake
The way we think about data security and integrity has been completely transformed by blockchain technology. Blockchain, at its heart, is a distributed, decentralized ledger that is used to store and verify transactions. As a result, there is no single entity in charge of managing the network, and each user has access to the same transaction history.
Consensus mechanisms are one of the fundamental characteristics that contribute to blockchain’s high level of security. These procedures are employed to make sure that everyone on the network concurs with the blockchain’s present state. Evidence of Work (PoW) and Evidence of Stake (EoS) are the two most widely used consensus procedures (PoS).
The initial consensus method in use with blockchain technology is called Proof of Work. Participants in this computational process must resolve challenging mathematical puzzles in order to add new blocks to the chain. The method is intended to be extremely challenging and time-consuming, making it difficult for one participant to completely control the network.
On the other side, Proof of Stake is a more modern consensus technique that is becoming more well-liked. In order to validate transactions and add new blocks to the chain, it requires participants to stake a particular amount of cryptocurrency. Participants who stake more cryptocurrencies have a higher chance of being chosen to validate transactions. This method is intended to be less prone to centralization and more energy-efficient than PoW.
Utilizing cryptographic methods like hashing and digital signatures is another important aspect of blockchain technology. One-way processes like hashing take an input and output a fixed-length result. This output, known as a hash, is specific to the input and will change totally if the input is even slightly altered. As an alternative, digital signatures are employed to demonstrate the legitimacy of a transaction. They operate by utilizing a corresponding public key to verify the signature and a private key to sign a transaction.
Another important aspect of blockchain technology’s security is its decentralization. The lack of centralized authority makes it far more challenging for an attacker to seize control of the network. Additionally, because the network is spread, there is no single point of failure, which greatly increases its resistance to attacks.
Another important aspect of blockchain technology is smart contracts. When specific criteria are met, these self-executing contracts are intended to take effect immediately. This has the potential to significantly improve the security and efficiency of many different sectors and use cases, including voting systems and supply chain management.
Blockchain technology does, however, provide a unique set of difficulties. Scalability is one of the main obstacles. The amount of data that needs to be saved and verified grows along with the network’s growing membership. This may result in lengthy transaction times and expensive fees.
Regulatory compliance is yet another issue that blockchain technology must address. Businesses and individuals that wish to adopt blockchain technology are experiencing uncertainty as a result of the fact that governments across the world are still finding out how to regulate this new technology.
Despite these difficulties, blockchain technology is a viable option for many different industries and use cases thanks to its security features. Consensus mechanisms, cryptographic methods, decentralization, and smart contracts all combine to provide a system that is extremely secure and robust.
We can anticipate the creation of quantum-resistant algorithms in the future, which will be able to fend off attacks from quantum computers. The security and usefulness of the system will also be improved by combining blockchain with other cutting-edge technologies like artificial intelligence and the Internet of Things.
The use of cryptographic techniques, such as hashing and digital signatures, to secure transactions on the blockchain
Blockchain technology is a decentralized system that enables safe and open transaction recording. Utilizing cryptographic methods is one of the main aspects of blockchain security. These methods, including hashing and digital signatures, aid in making sure that blockchain transactions are impervious to manipulation and cannot be changed by malevolent parties.
An input, such as a transaction, is transformed into a fixed-length output, known as a hash, through the process of hashing. Any modification to the input will produce an entirely different hash because the hash is specific to the input. This makes it simple to find any alterations or tampering with a blockchain transaction.
On the other hand, digital signatures are employed to guarantee the legitimacy of transactions. A user’s private key is used to sign a transaction, and the accompanying public key is used to verify the signature. This is how they operate: using a private and public key system. This guarantees that a transaction can only be authorized by its owner and that it has not been tampered with.
The integrity of transactions on the blockchain is supported by the application of various cryptographic methods. This is crucial for the security of blockchain systems because it ensures that once a transaction has been recorded on the blockchain, it cannot be changed or interfered with by malevolent parties.
The decentralization of blockchain systems, in addition to cryptographic methods, increases their security. One point of failure exists in a centralized system, which makes it vulnerable to attack by bad actors. A decentralized system, on the other hand, lacks a single point of failure, which makes it considerably more challenging for attackers to bring down the system.
Another essential component of blockchain technology that can improve security is smart contracts. When specific criteria are met, a smart contract is computer software that automatically carries out the provisions of a contract. This can be used to automate intricate corporate procedures and eliminate the need for middlemen, increasing security and lowering the likelihood of fraud.
In business and industrial settings, the usage of private, permissioned blockchain networks is also rising in popularity. These networks are more secure than open blockchain networks since access is limited to a particular group of users. Additionally, they can automate difficult commercial procedures like supply chain management and hold sensitive data.
Blockchain technology has numerous security characteristics, however, there are still issues that need to be resolved. For instance, scaling is a significant issue for blockchain systems. The system may grow slow and clogged as more people join the network and more transactions are made. Since governments all over the world are still finding out how to manage blockchain networks, regulatory compliance is also an issue.
The importance of decentralization in enhancing the security of blockchain systems
A decentralized digital ledger using blockchain technology keeps track of transactions made among a number of computers. The capacity of blockchain to offer a high level of security for the transactions it records is one of its primary benefits. We shall examine the various cryptographic methods used to secure blockchain transactions in this post.
Hashing is one of the most significant cryptographic methods utilized in blockchain technology. A mathematical technique known as a “hash function” takes an input (or “message”) and outputs a fixed-length character string known as the “hash” or “digest.” The 64-character hexadecimal output of the SHA-256 hash function used in the Bitcoin blockchain is utilized. It is practically hard to change the contents of a block after it has been added to the blockchain since the hash function assures that any change in the input will result in a completely different output.
Digital signatures are another significant cryptographic method utilized in blockchain technology. A person can demonstrate both their identity and the veracity of a message they have transmitted by using a digital signature, which is a mathematical technique. Digital signatures are used in the blockchain context to sign transactions, ensuring that only the owner of a specific private key can authorize a transaction. This stops money from being spent without authorization and gives the blockchain a high level of security.
Blockchain technology uses Proof of Work (PoW), a consensus process, in addition to these cryptographic methods to safeguard its network. In a proof-of-work (PoW) system, users have to put in a specific amount of computational labor before they can add a new block to the blockchain. The purpose of this labor, known as mining, is to make it prohibitively expensive for malevolent actors to alter the blockchain.
Proof of Stake is an additional consensus method employed by blockchain technology (PoS). In a proof-of-stake (PoS) system, users are required to possess a specific quantity of bitcoin before they may add a new block to the blockchain. This technique uses less energy than PoW and deters bad actors from altering the blockchain by making it prohibitively expensive to do so.
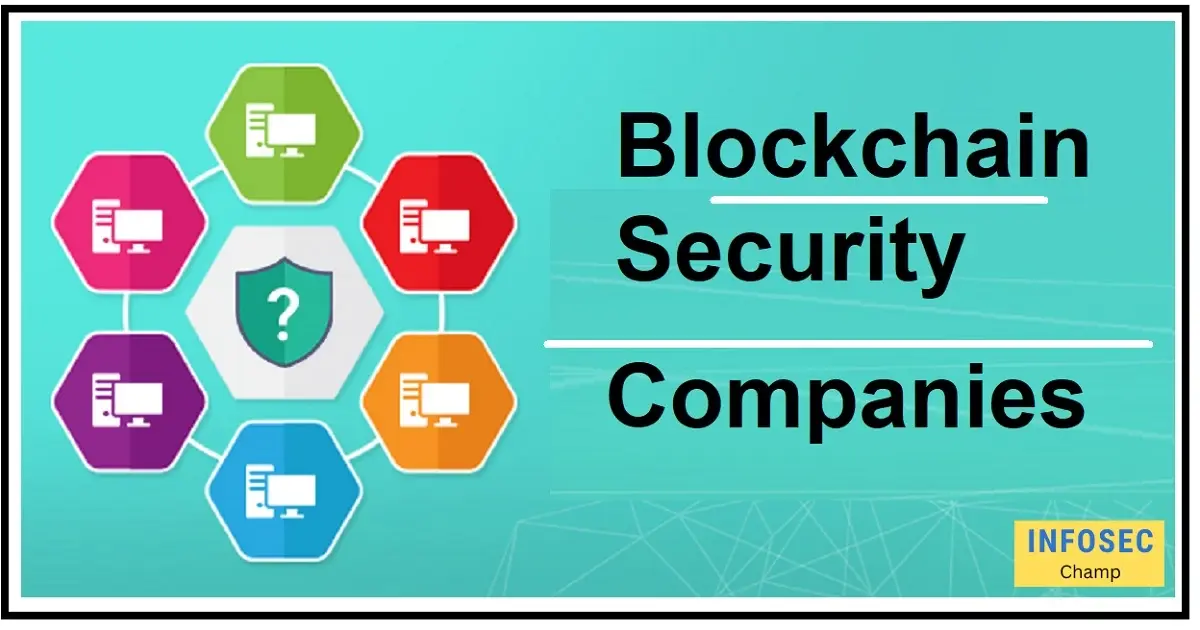
Top 25 blockchain security companies
- Chainalysis
- Bitfury
- CipherTrace
- Elliptic
- ChainGuardian
- Slowmist
- Blockchain Intelligence Group
- Hosho
- PeckShield
- Anchain.AI
- CertiK
- Quantstamp
- Solidified
- ConsenSys Diligence
- Crypto Aware
- Blocksafe Alliance
- NXM Labs
- Certik
- BlockSafe Technologies
- Polymath
- SecureLayer7
- Digital Asset
- ChainSecurity
- ChainGuardian
- BitGo
The use of smart contracts in blockchain systems and their potential impact on security
The way we do business and maintain data has been completely transformed by blockchain technology. The capacity of blockchain to safeguard data through the use of smart contracts is one of its fundamental characteristics. In smart contracts, the details of the agreement between the buyer and seller are directly encoded into lines of code. These contracts self-execute. These contracts are tamper-proof, transparent, and simple to verify because they are duplicated and kept on the blockchain network.
Smart contracts offer a mechanism to automatically carry out a contract if specific requirements have been completed. A smart contract, for instance, might be used to automatically transfer ownership of a property from the seller to the buyer once the predetermined payment is made. This decreases the possibility of fraud and mistakes and eliminates the need for middlemen.
The management of the supply chain might be considerably enhanced by smart contracts. All participants in a supply chain can have access to real-time information about the whereabouts and status of goods by using smart contracts, which lowers the possibility of delays or mistakes. Additionally, this can increase accountability and transparency, making it simpler to track down the source of products and identify any potential issues.
Financial services like lending and insurance can also employ smart contracts. For instance, after certain requirements are satisfied, such as the submission of the required papers, a smart contract can automatically initiate the reimbursement of an insurance claim. The time and expense related to processing claims can be significantly decreased in this way. The underwriting and loan origination processes can also be automated with the help of smart contracts, which lowers the risk of fraud and errors.
Healthcare is another industry with potential use for smart contracts. Patients can have more control over their personal health information by using smart contracts, enabling them to only share it with healthcare professionals who need to know. This can decrease the risk of privacy violations while increasing the effectiveness of healthcare delivery.
Smart contracts include a wide range of potential advantages, but there are also issues that need to be resolved. Making sure that smart contracts are secure is one of the major difficulties. Smart contracts are susceptible to faults and defects, just like any other software. If a bug in a smart contract is discovered, it might be used by hackers to steal money or interfere with the contract.
Making smart contracts interoperable is another difficulty. Due to the technology’s quick evolution, there are currently a wide variety of blockchain platforms, each with its own set of guidelines and regulations. This may limit the usage of smart contracts in practical applications and make it difficult for them to communicate with one another.
The role of private and permissioned blockchain networks in enterprise and industrial contexts
Blockchain technology offers a secure, decentralized method of data storage and movement, which has the potential to transform a number of industries. The usage of smart contracts is a crucial component of blockchain security.
In smart contracts, the details of the agreement between the buyer and seller are directly encoded into lines of code. These contracts self-execute. They can be automatically performed when specific circumstances are satisfied and are duplicated and kept on the blockchain network. As a result, transactions can be carried out more quickly and securely, lowering the risk of fraud and eliminating the need for middlemen.
The capacity of smart contracts to automate the process of enforcing contract obligations is one of their main advantages. For instance, a smart contract can automatically transfer ownership of a property from the seller to the buyer after payment has been received in a real estate transaction. This can drastically cut down on the time and expense of the transaction by doing away with the requirement for a third-party mediator like a lawyer or real estate agent.
Another advantage of smart contracts is that they make it easier to develop decentralized applications (dApps). Supply chain management, voting processes, and online marketplaces are just a few examples of the many uses for decentralized applications (dApps), which are programs that run on a blockchain network rather than a central server.
The security of transactions may also be increased using smart contracts. They are protected from fraud and tampering since they are kept on a decentralized network. Additionally, using digital signatures and other cryptographic methods can guarantee that only parties with the proper permissions can access and utilize the contract.
Despite the advantages of smart contracts, there are still difficulties in implementing them. The absence of industry standards is one of the biggest problems. It is challenging for developers to create decentralized applications (dApps) that are interoperable with many blockchain platforms because each one, including Ethereum and EOS, has its own distinct programming languages and protocols.
40 Best practices for Blockchain attacks for Blockchain security
- Use the most recent security patches and upgrades to keep your software and systems up to date.
- For all user accounts, employ multi-factor authentication
- For all user accounts, use a solid, one-time password.
- Put your cryptocurrency in a hardware wallet and manage it there.
- Keep the private keys to your bitcoin wallets in cold storage. offline
- To safeguard your internet connection, utilize a trustworthy and trusted VPN provider.
- Use a trustworthy and dependable firewall to safeguard your network.
- To secure your systems, choose antivirus software that is reputable and trustworthy.
- To safeguard your systems, use an effective intrusion detection and prevention solution.
- Use trustworthy encryption software to keep your data safe.
- To safeguard your systems, use a recognized and trustworthy DDoS protection provider.
- To safeguard your web applications, use a trustworthy web application firewall.
- To safeguard your email, use a trusted and recognized email security solution.
- To safeguard your mobile devices, use a trustworthy mobile device management program.
- To safeguard your systems, choose an effective endpoint protection solution.
- For the protection of your cloud-based systems, use a reputable and trustworthy cloud security solution.
- To safeguard your network, use a reputable and trustworthy network security solution.
- Control user access by utilizing a trustworthy identity and access management system.
- To safeguard your data, use a credible and trustworthy data loss prevention system.
- To keep an eye on your systems, choose a trusted and dependable security information and event management solution (SIEM).
- Utilize a trustworthy security operations center solution to track and address security events.
- Respond to security incidents by using a renowned and trustworthy incident response plan.
- To check your systems for vulnerabilities, use a trustworthy and reliable penetration testing provider.
- To learn about fresh and developing risks, use a trustworthy threat intelligence provider.
- To teach your staff about security best practices, use a dependable and trustworthy security awareness training service.
- To direct your security efforts, use a trustworthy security governance framework.
- To prove that you are following security regulations, use a trustworthy security certification.
- Use a reputable and reliable security risk management framework to identify and manage security risks
- Use a reputable and reliable security incident management framework to manage security incidents
- Use a reputable and reliable security compliance management framework to manage compliance with security regulations and standards
- Use a reputable and reliable security incident response plan to respond to security incidents
- Use a reputable and reliable security incident response team to respond to security incidents
- Use reputable and reliable security incident management software to manage security incidents
- Use reputable and reliable security monitoring software to monitor your systems
- Use a reputable and reliable security incident response automation software to automate incident response tasks
- Use reputable and reliable security incident response training to train your employees on incident response procedures
- Use reputable and reliable security incident response testing to test your incident response plan and procedures
- Use a reputable and reliable security incident response certification to demonstrate your incident response capabilities
- Use a reputable and reliable security incident response service to outsource incident response tasks
- Use a reputable and reliable security incident response consulting service to get expert advice and guidance on incident response.
The challenges facing blockchain security, such as scalability and regulatory compliance.
Scalability is one of the biggest issues facing blockchain technology. A blockchain network can get clogged and slow as the number of users and transactions grows. A blockchain-based system may not be able to support a huge number of users or a high volume of transactions as a result.
For public blockchain networks like Bitcoin and Ethereum, where anybody can join and participate, the scalability issue is very important. These networks can grow slow and crowded when more users and transactions are added because of the increased volume of data that needs to be processed and stored. Due to this, users may have to pay expensive fees and endure protracted wait times before their transactions are approved.
The size of the blockchain itself is another scalability issue. The amount of storage space needed to hold the complete blockchain grows as more transactions are added to it. Users with less storage space, including those using mobile devices, may find it challenging to use the network as a result.
Off-chain transactions, sharding, and the use of sidechains are just a few of the ideas that have been suggested to solve the scalability problem. Off-chain transactions enable some transactions to be handled away from the blockchain, which can greatly minimize the amount of data that needs to be processed and stored on the blockchain. The practice of “sharding” entails breaking the blockchain into smaller, or “shard,” portions that may be processed simultaneously, hence boosting the network’s total throughput. The primary blockchain is connected to sidechains, which are independent blockchain networks with more processing and storage capacity.
Regulatory compliance is a problem that blockchain technology also faces. Regulations pertaining to blockchain technology are continually being developed and improved as it is still a relatively new and evolving technology. In particular, governments and regulatory agencies may find it challenging to enforce current rules and regulations, such as those pertaining to money laundering and terrorism funding, due to the decentralized structure of blockchain networks.
Some blockchain initiatives are opting for a more centralized approach to handle these issues, with a single organization regulating access to the network and enforcing adherence to current regulations. Others are collaborating with legislators and regulatory organizations to create new rules and legislation that take into consideration the special features of blockchain technology.
The future of blockchain security, including the development of quantum-resistant algorithms and the integration of blockchain with other emerging technologies
As the technology develops and becomes more widely used, blockchain security is a subject of tremendous interest and worry. The potential for quantum computing to compromise the cryptographic techniques used to safeguard transactions on the blockchain is one of the main challenges facing blockchain security. Quantum computers are expected to surpass conventional computers in speed as they develop in strength, making it possible for them to break the encryption protecting blockchain transactions.
Researchers and programmers are striving to create quantum-resistant algorithms that can withstand the power of quantum computers in order to solve this problem. The usage of post-quantum cryptography, which employs challenges thought to be challenging for quantum computers to solve, and the incorporation of quantum key distribution (QKD) into blockchain systems are a couple of potential remedies. QKD possibly resists quantum attacks by allowing the secure distribution of encryption keys using quantum mechanical principles.
Integration of blockchain with other cutting-edge technologies, such as artificial intelligence (AI) and the Internet of Things, is another area of focus for blockchain security (IoT). By enabling smart contracts to self-execute depending on predetermined parameters and conditions, for instance, the combination of blockchain with AI can increase the security of these contracts. By enabling these devices to share data and communicate securely, the integration of blockchain with IoT can also improve the security of these gadgets.
Integrating blockchain technology with established cybersecurity tools like firewalls and intrusion detection systems can also increase blockchain security. This can aid in the prompt and effective detection of potential security risks and vulnerabilities.
Blockchain security is still a tough and continuous task despite these advancements. It will be crucial for academics, developers, and users to keep up with the most recent trends and advancements in blockchain security as the technology continues to develop and find widespread use. For blockchain systems to remain safe and secure, it will be essential to stay current on the most recent security threats, vulnerabilities, novel solutions, and best practices.


