In order to detect security risks and take appropriate action, SIEM (Security Information and Event Management) is a security solution that gathers and examines various log data from devices, systems, and applications used by an organization. Additionally, it aids businesses in adhering to numerous legal and security requirements.
Typically, SIEM consists of the following elements:
- Event logs: Events that take place on devices, systems, and applications within an organization are recorded in event logs.
- Security analytics: Analysis of event logs to spot patterns and trends that can point to security vulnerabilities is known as “security analytics.”
- Incident response: The process of responding to and managing security incidents, such as online attacks, is referred to as incident response.
- Compliance reporting: Compliance reporting is the practice of creating reports that show how well a business complies with certain security and legal requirements.
SIEM solutions are often used by large organizations to centralize and monitor the security of their networks and systems. They can help organizations identify and respond to security threats in a timely manner, as well as to meet regulatory requirements for data security and privacy.
The full form of SIEM is Security Information and Event Management. Security Information and Event Management refers to a security solution that combines and analyzes various log data from devices, systems, and applications within an organization to identify security threats and respond to them. It also helps organizations to comply with various security and regulatory standards.
How SIEM works?
In order for SIEM systems to function, log data from various devices, systems, and applications within an organization must be collected and analyzed. This log data contains details regarding actions taken by users, file accesses, and system failures, among other actions taken by various devices, systems, and applications.
This log data is processed by the Security Information and Event Management system, which also applies various analytics and algorithms to look for patterns and trends that could be signs of security concerns. For instance, the system might flag this as a possible security problem if it notices a high volume of unsuccessful login attempts coming from a single IP address.
The SIEM system can respond to a possible security issue in a number of ways after it has been recognized. These procedures could involve sending out a warning, restricting access to a certain resource, or starting an incident response procedure.
Security Information and Event Management systems can be used to produce reports that show a company is in compliance with different security and regulatory standards in addition to detecting and responding to security threats. For large firms that must adhere to tight compliance regulations, this might be very helpful.
How to design a SIEM?
There are several processes involved in designing a SIEM (Security Information and Event Management) system, including:
- Identify the organization’s security needs: Find out what kind of security the company needs: The first stage in building a Security Information and Event Management system is to find out what kind of security the organization specifically needs. To do this, it may be necessary to specify the data types that must be gathered and evaluated as well as the precise security dangers that the firm is most worried about.
- Determine the sources of log data: Finding the sources of log data is the next step. These are the log data sources that the SIEM system will employ. This could comprise internal organizational tools, systems, and programs as well as external data sources like threat intelligence feeds.
- Configure the SIEM system: How to set up the SIEM system: After determining the log data’s sources, you must set up the SIEM system to capture and analyze the data. Setting up connectors or agents to gather log data from various sources, as well as configuring analytics and algorithms to find patterns and trends that could point to security issues, are possible steps in this process.
- Set up alerting and incident response processes: Create alerting and incident response procedures: It’s critical to create procedures for reacting to security risks that the SIEM system has detected. This could entail building an incident response strategy for managing and responding to security incidents, as well as putting up alerts to notify pertinent individuals when a potential threat is found.
- Test and fine-tune the SIEM system: After the Security Information and Event Management system has been built and set up, it is crucial to run tests on it to make sure everything is running smoothly and that it is correctly identifying potential risks. This can entail modeling different security situations and evaluating the outcomes to gauge how well the SIEM system functions. To make the system more precise and efficient, you may need to make adjustments.

What are some of the challenges with legacy SIEM solutions?
Some of the challenges with legacy SIEM (Security Information and Event Management) solutions include:
- Complexity: Legacy SIEM systems can be complex to set up and maintain, requiring specialized knowledge and expertise to configure and manage them effectively.
- High costs: Legacy SIEM solutions can be expensive to implement and maintain, particularly for large organizations with complex security needs.
- Limited scalability: Legacy SIEM systems may not be able to scale effectively to meet the needs of rapidly growing organizations, resulting in a lack of visibility into security threats and potential compliance issues.
- Limited capabilities: Legacy SIEM solutions may not have the capabilities needed to effectively detect and respond to modern security threats, such as advanced persistent threats (APTs) or zero-day vulnerabilities.
- Limited integration: Legacy SIEM systems may not integrate easily with other security solutions or applications, resulting in a fragmented security landscape.
As a result of these challenges, many organizations are turning to modern, cloud-based Security Information and Event Management solutions that offer greater scalability, capabilities, and integration with other security solutions.
How to Build Your Own SIEM?
Building your own SIEM (Security Information and Event Management) system involves the following steps:
- Identify the organization’s security needs: The first step in building a Security Information and Event Management system is to identify the organization’s specific security needs and requirements. This may include identifying the types of data that need to be collected and analyzed, as well as the specific security threats that the organization is most concerned about.
- Determine the sources of log data: Next, you need to determine the sources of log data that will be used by the Security Information and Event Management system. This may include devices, systems, and applications within the organization, as well as external data sources such as threat intelligence feeds.
- Choose a SIEM platform: There are a number of Security Information and Event Management platforms available, ranging from open-source options to commercial solutions. You will need to choose a platform that meets the organization’s security needs and fits within your budget.
- Configure the SIEM system: Once you have chosen a Security Information and Event Management platform, you will need to configure it to collect and process the log data from the various sources you have identified. This may involve setting up connectors or agents to collect log data from various sources, as well as configuring analytics and algorithms to identify patterns and trends that may indicate security threats.
- Set up alerting and incident response processes: It is important to establish processes for responding to security threats that are identified by the SIEM system. This may involve setting up alerts to notify relevant personnel when a potential threat is detected, as well as establishing an incident response process for managing and responding to security incidents.
- Test and fine-tune the SIEM system: Once the SIEM system has been configured and set up, it is important to test it to ensure that it is working properly and identifying potential threats accurately. This may involve simulating various security scenarios and analyzing the results to see how the Security Information and Event Management system performs. If necessary, you may need to fine-tune the system to improve its accuracy and effectiveness.
Help the personnel fight against security threats
There are a number of ways that SIEM (Security Information and Event Management) systems can help personnel fight against security threats, including:
- Identifying potential threats: SIEM systems analyze log data from various devices, systems, and applications within an organization to identify patterns and trends that may indicate security threats. This can help personnel to be aware of potential threats and take steps to mitigate them.
- Generating alerts: SIEM systems can generate alerts when potential threats are detected, allowing personnel to be notified and take action to respond to the threat.
- Providing visibility: SIEM systems provide a centralized view of security activity across an organization, which can help personnel to identify potential threats more easily and respond to them more effectively.
- Simplifying compliance: SIEM systems can generate reports that demonstrate an organization’s compliance with various security and regulatory standards, which can help personnel to ensure that the organization is meeting these requirements and to take corrective action if necessary.
- Improving incident response: SIEM systems can be integrated with incident response processes, allowing personnel to more effectively manage and respond to security incidents when they occur.
Who uses SIEM?
SIEM (Security Information and Event Management) systems are primarily used by large organizations to centralize and monitor the security of their networks and systems. These organizations may include:
- Enterprises: Large enterprises with complex networks and systems may use Security Information and Event Management systems to monitor and secure their IT infrastructure.
- Government agencies: Government agencies may use Security Information and Event Management systems to ensure the security of their networks and systems, as well as to meet various regulatory requirements.
- Healthcare organizations: Healthcare organizations may use Security Information and Event Management systems to secure sensitive patient data and comply with various regulatory standards.
- Financial institutions: Financial institutions may use SIEM systems to secure financial data and meet regulatory requirements related to data security and privacy. (check on financial cyber security also)
- Educational institutions: Educational institutions may use Security Information and Event Management systems to secure student and faculty data and comply with various regulatory standards.
- Service providers: Service providers, such as cloud providers and managed security service providers, may use Security Information and Event Management systems to secure their networks and systems and provide secure services to their customers.
Which SOC team is responsible for the implementation and ongoing maintenance of the Secops team including SIEM and analysis tools?
The SOC (Security Operations Center) team is normally in charge of setting up and maintaining the Secops team’s tools for analysis and SIEM (Security Information and Event Management).
In addition to responding to security threats and incidents as they arise, the SOC team is in charge of continuously monitoring and managing the security posture of a business. Assist in identifying and responding to security risks, this includes implementing and maintaining various security tools and technology, such as SIEM systems and analysis tools.
In order to guarantee that security threats are successfully managed and mitigated, the SOC team may also be in charge of overseeing the incident response procedure and working with other teams within the organization. The SOC team may also be in charge of producing reports and proving compliance with different security and regulatory standards.

Top 25 SIEM vendors & players | What are popular SIEM platforms?
Some popular Security Information and Event Management vendors include (as per Gartner):
- Splunk
- IBM Security QRadar
- Microsoft
- Securonix
- Exabeam
- LogRhythm
- AlienVault USM
- ArcSight
- Fortinet
- Sumo Logic
- Datadog
- ManageEngine EventLog Analyzer
- LogPoint
- Graylog
- Zoho ManageEngine EventLog Analyzer
- Exabeam
- Rapid7
- Siemplify
- FireEye Helix
- SolarWinds
- Stealthwatch
- McAfee Enterprise Security Manager
- RSA NetWitness
- Micro Focus ArcSight
- Elastic
How do you prevent a false positive for SIEM?
There are several ways to prevent false positives in a SIEM (Security Information and Event Management) system:
- Use multiple detection techniques: By using multiple techniques to detect security events, you can reduce the likelihood of false positives.
- Fine-tune your rules and policies: Carefully crafting your rules and policies can help reduce false positives by ensuring that only relevant events are flagged.
- Implement anomaly detection: Anomaly detection algorithms can help identify unusual activity that may be indicative of a security event.
- Use context to validate alerts: By using contextual information, you can validate alerts and reduce the likelihood of false positives.
- Use machine learning: Machine learning algorithms can be trained to identify normal patterns of behavior, helping to reduce false positives.
- Incorporate user and entity behavior analytics (UEBA): UEBA can help identify unusual patterns of behavior that may indicate a security event, reducing false positives.
- Implement a correlation engine: A correlation engine can help identify patterns of activity that may indicate a security event, reducing false positives.
How does the SIEM tool handle the issue of completeness of the log?
A SIEM (Security Information and Event Management) solution is made to gather and examine logs from a variety of sources inside the IT architecture of a company. The Security Information and Event Management tool often has capabilities like these to assure the completeness of logs:
- Data collection agents: These agents are installed on servers and devices throughout the network to collect logs and send them to the SIEM for analysis.
- Data normalization: The SIEM tool can normalize log data from different sources, making it easier to analyze and compare logs from different systems.
- Log forwarding: The SIEM tool can forward logs to other systems or tools for further analysis or archiving.
- Log retention: The SIEM tool can retain logs for a specified period of time, allowing you to go back and review log data from the past.
A Security Information and Event Management platform can assist in ensuring that logs are gathered from all pertinent sources and are stored for long enough to permit an in-depth analysis by using these features.
What is the description of SIEM event aggregation?
The process of gathering and aggregating security-related events and logging data from diverse sources inside an organization’s IT infrastructure is known as SIEM (Security Information and Event Management) event aggregation. Events and logs from servers, workstations, networking appliances, security appliances, and other systems may be included in this.
By gathering all pertinent security data in one location, event aggregation aims to provide a centralized view of an organization’s security posture. This enables security analysts to recognize patterns of behavior and potential security threats quickly, as well as to respond appropriately to lessen those threats.
Data collection agents, which are deployed on network servers and other devices to collect logs and transfer them to the SIEM for analysis, are frequently used in event aggregation. The log data is then processed by the Security Information and Event Management application and displayed in a central dashboard or console for security analysts to analyze.

Top 15 Best Practices for SIEM Solution
Here are 15 best practices for implementing and maintaining a SIEM (Security Information and Event Management) solution:
- Start with a clear understanding of your security objectives: Determine the specific security goals that you want to achieve with your SIEM, such as detecting and responding to threats, compliance, or incident response.
- Conduct a thorough assessment of your current security posture: Before implementing a SIEM, conduct an assessment of your current security posture to identify any gaps or weaknesses that the Security Information and Event Management can help address.
- Gather and normalize data from all relevant sources: To get the most value from your SIEM, it is important to gather and normalize data from all relevant sources within your IT infrastructure. This includes servers, workstations, network devices, and applications.
- Define clear rules and policies: Establish clear rules and policies in the Security Information and Event Management to specify which types of events should be flagged and how they should be handled. This will help ensure that the SIEM is correctly identifying and alerting on relevant events.
- Test and validate the SIEM regularly: Regular testing and validation of the Security Information and Event Management is important to ensure that it is functioning correctly and providing accurate and actionable information.
- Monitor and maintain the SIEM: Ongoing monitoring and maintenance is important to ensure that the SIEM remains effective over time. This may include adjusting rules and policies as needed, and testing and validating the Security Information and Event Management on a regular basis.
- Integrate the SIEM with other security tools and systems: Consider integrating the SIEM with other security tools and systems, such as intrusion detection systems, incident response platforms, and vulnerability scanners, to get a more comprehensive view of your security posture.
- Train security analysts on how to use the SIEM effectively: Ensure that your security team has the knowledge and skills to use the SIEM effectively, including understanding how to interpret log data and respond to alerts.
- Establish clear roles and responsibilities: Define clear roles and responsibilities for using and managing the Security Information and Event Management within your organization.
- Implement a robust incident response process: Develop and implement a robust incident response process that includes procedures for responding to alerts and other security events generated by the Security Information and Event Management.
- Regularly review and update your rules and policies: Review and update your rules and policies on a regular basis to ensure that they are still relevant and effective.
- Use a combination of manual and automated processes: Utilize both manual and automated processes for managing and responding to security events, as appropriate.
- Implement strong access controls: Ensure that access to the Security Information and Event Management is restricted to authorized personnel only, and implement strong access controls to prevent unauthorized access.
- Regularly review and update your security posture: Regularly review and update your overall security posture to identify any changes or improvements that may be needed.
- Seek out additional training and resources: Make sure that your security team has access to the
How to integrate with SIEM?
There are several steps you can follow to integrate a new system or device with a SIEM (Security Information and Event Management) tool:
- Determine the log sources: Identify the systems or devices that you want to integrate with the SIEM, and determine what types of logs they generate.
- Configure log collection: Configure the systems or devices to send their logs to the Security Information and Event Management using Syslog, a data collection agent, or another method.
- Normalize log data: If necessary, use the SIEM’s log normalization capabilities to ensure that the logs from different sources are in a consistent format.
- Set up rules and policies: Define rules and policies in the Security Information and Event Management to specify which types of events should be flagged and how they should be handled.
- Test and validate: Test the integration to ensure that logs are being collected and processed correctly and validate the results to ensure that the SIEM is correctly identifying and flagging relevant events.
- Monitor and maintain: Ongoing monitoring and maintenance is important to ensure that the integration remains effective over time. This may include adjusting rules and policies as needed, and testing and validating the integration on a regular basis.
What is a SIEM collector?
A software component known as a SIEM (Security Information and Event Management) collector is in charge of gathering log data from numerous sources throughout an organization’s IT infrastructure. The collector normally runs on a dedicated server or appliance that is linked to the different log sources via networks or data collection agents.
The collector often handles a variety of duties, such as:
- Receiving log data from the log sources
- Normalizing the log data to ensure it is in a consistent format
- Storing the log data in a centralized repository
- Forwarding the log data to other systems or tools for further analysis or archiving
- The collector is an important part of a SIEM system, as it is responsible for gathering all of the relevant log data from throughout the network and making it available for analysis by security analysts.
Which protocol can be used to send information to a SIEM server?
There are several protocols that can be used to send information to a SIEM (Security Information and Event Management) server:
- Syslog: Syslog is a widely used protocol for sending log data over a network. It is supported by a wide range of devices and systems, making it a popular choice for sending log data to Security Information and Event Management.
- SNMP: Simple Network Management Protocol (SNMP) can be used to send log data and other types of information from network devices to a SIEM.
- syslog-ng: syslog-ng is an open-source log management platform that can be used to send log data to Security Information and Event Management.
- rsyslog: rsyslog is another open-source log management platform that can be used to send log data to Security Information and Event Management.
- Custom API: Some SIEMs may provide a custom API that can be used to send log data or other types of information to the Security Information and Event Management.
Ultimately, the choice of the protocol will depend on the specific needs and capabilities of your organization and the systems and devices that you want to integrate with the SIEM.
Defender for cloud apps display a status of disconnected for the SIEM?
Defender for Cloud Apps’ “disconnected” status for a SIEM (Security Information and Event Management) integration often denotes that there is a problem with the connection between Defender and the SIEM. This could be caused by a number of things, such as network problems, configuration issues, or a fault with the SIEM itself.
You may want to attempt the following actions to solve the problem:
- Check the network connection: Make sure that the network connection between the Defender and the Security Information and Event Management is stable and reliable.
- Check the integration configuration: Verify that the integration is configured correctly in both Defender and Security Information and Event Management.
- Check the SIEM logs: Review the logs from the SIEM to see if there are any error messages or other indicators of a problem.
- Contact support: If you are unable to resolve the issue on your own, you may want to contact the support team for Defender or the SIEM for further assistance.
You should be able to identify the reason for the disconnect by using the methods listed above, and you can then take the necessary action to fix the problem.
How to configure SIEM in Linux?
Here are the general steps for configuring a SIEM (Security Information and Event Management) tool on a Linux system:
- Install the SIEM software: Follow the instructions provided by the SIEM vendor to install the software on your Linux system.
- Configure data collection: Set up data collection agents or configure the systems and devices on your network to send their logs to the SIEM using syslog or another method.
- Normalize log data: Use the SIEM’s log normalization capabilities to ensure that the logs from different sources are in a consistent format.
- Set up rules and policies: Define rules and policies in the Security Information and Event Management to specify which types of events should be flagged and how they should be handled.
- Test and validate: Test the SIEM to ensure that logs are being collected and processed correctly, and validate the results to ensure that the SIEM is correctly identifying and flagging relevant events.
- Monitor and maintain: Ongoing monitoring and maintenance is important to ensure that the Security Information and Event Management remains effective over time. This may include adjusting rules and policies as needed, and testing and validating the SIEM on a regular basis.
AWS SIEM
AWS Security Hub is a SIEM (Security Information and Event Management) solution offered by Amazon Web Services (AWS), along with other security-related tools and services.
The AWS Security Hub serves as a consolidated location for managing security alerts and discoveries from both AWS accounts and external security products. You may use it to browse, sort, and take action on security warnings and discoveries across all of your AWS accounts. To give you a complete picture of your security posture, Security Hub also interfaces with other AWS services like Amazon GuardDuty, Amazon Inspector, and AWS Firewall Manager (or WAF).
The cost of AWS Security Hub is a subscription service, and it depends on how many discoveries and alarms the service processes. Visit the AWS Security Hub page on the AWS website for further details.
Azure SIEM
Microsoft’s cloud-native SIEM (Security Information and Event Management) product is called Azure Sentinel. It is intended to support businesses in detecting, looking into, and handling dangers in their hybrid environments.
A centralized view of security data from numerous sources, such as Azure resources, on-premises systems, and outside security technologies, is provided by Azure Sentinel. To identify potential risks and uncover anomalous patterns of activity, it employs machine learning algorithms.
The cost of Azure Sentinel is a subscription service, and it depends on how many events and alarms are handled by the service. Visit the Azure Sentinel page on the Azure website for further details.
Which Azure service can you use as security information and event management SIEM?
The security information and event management (SIEM) tool offered by Microsoft Azure is called Azure Sentinel. It is a cloud-native SIEM that supports businesses in identifying, researching, and handling risks in their hybrid settings.
A centralized view of security data from numerous sources, such as Azure resources, on-premises systems, and outside security technologies, is provided by Azure Sentinel. To identify potential risks and uncover anomalous patterns of activity, it employs machine learning algorithms. The cost of Azure Sentinel is a subscription service, and it depends on how many events and alarms are handled by the service.
How to implement a SIEM?
Implementing a SIEM (Security Information and Event Management) system typically involves the following steps:
- Determine your security objectives: Identify the security goals that you want to achieve with your SIEM, such as detecting and responding to threats, compliance, or incident response.
- Assess your current security posture: Conduct an assessment of your current security posture to identify any gaps or weaknesses that the SIEM can help address.
- Select a SIEM solution: Research and compare different SIEM solutions to determine which one is the best fit for your organization’s needs and budget.
- Set up data collection: Configure the systems and devices on your network to send their logs to the Security Information and Event Management using syslog or another method.
- Normalize log data: Use the SIEM’s log normalization capabilities to ensure that the logs from different sources are in a consistent format.
- Set up rules and policies: Define rules and policies in the Security Information and Event Management to specify which types of events should be flagged and how they should be handled.
- Test and validate: Test the Security Information and Event Management to ensure that logs are being collected and processed correctly, and validate the results to ensure that the SIEM is correctly identifying and flagging relevant events.
- Monitor and maintain: Ongoing monitoring and maintenance is important to ensure that the SIEM remains effective over time. This may include adjusting rules and policies as needed, and testing and validating the Security Information and Event Management on a regular basis.
Which Azure service can you use as a security information and event management solution AZ 900?
The security information and event management (SIEM) tool offered by Microsoft Azure is known as Azure Sentinel. A cloud-native SIEM called Azure Sentinel aids businesses in identifying, researching, and dealing with risks in btheir hybrid settings.
It offers a centralized view of security information gathered from numerous sources, such as Azure resources, on-premises systems, and outside security tools. In order to identify potential threats and identify anomalous patterns of activity, Azure Sentinel employs machine learning algorithms.
You can read up on Azure Sentinel in the documentation or pass an Azure certification test like the Azure Fundamentals (AZ-900) exam to gain additional knowledge about it. The AZ-900 exam may feature questions about Azure Sentinel and other Azure security services. It covers a broad spectrum of Azure ideas and technologies, including security.
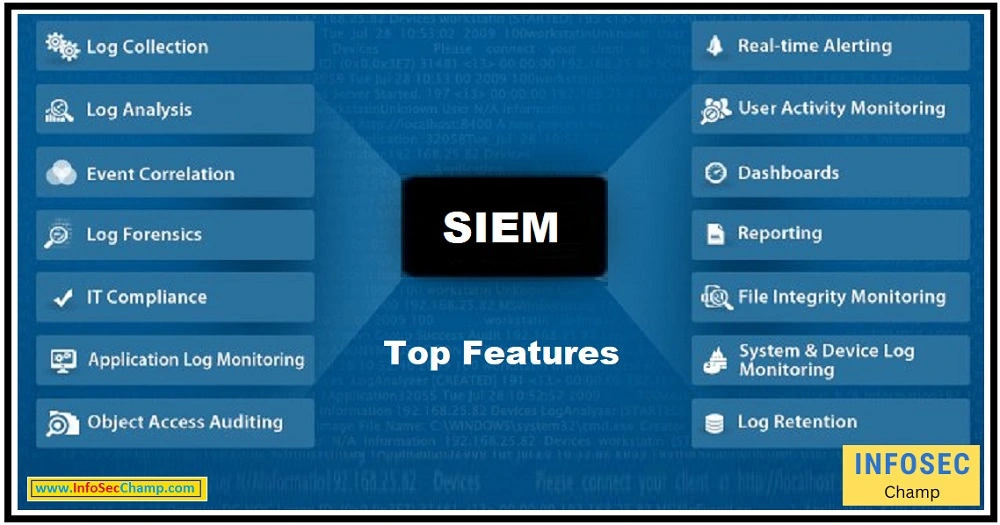
What are the top 25 features of SIEM?
Here are 25 features that are commonly found in SIEM (Security Information and Event Management) solutions:
- Event collection and aggregation: The ability to collect and combine security-related events and log data from various sources within an organization’s IT infrastructure.
- Data normalization: The ability to standardize log data from different sources, making it easier to analyze and compare logs from different systems.
- Event correlation: The ability to identify patterns of activity and potential security threats by analyzing logs and events from multiple sources.
- Rule-based alerting: The ability to create rules and policies that specify which types of events should be flagged and how they should be handled.
- Anomaly detection: The ability to identify unusual patterns of behavior that may indicate a security event.
- User and entity behavior analytics (UEBA): The ability to identify unusual patterns of behavior by individual users or entities that may indicate a security event.
- Compliance reporting: The ability to generate reports to demonstrate compliance with various regulations and standards.
- Threat intelligence integration: The ability to incorporate threat intelligence feeds and other sources of information to help identify potential threats.
- Security analytics: The ability to analyze security data using machine learning algorithms and other techniques to identify patterns and trends.
- Forensics and investigation tools: Tools and features to help security analysts investigate and respond to security events.
- Security orchestration and automation: The ability to automate the response to security events and reduce the time required to investigate and respond.
- Vulnerability management: The ability to identify and prioritize vulnerabilities within an organization’s IT infrastructure.
- Asset management: The ability to track and manage the assets within an organization’s IT infrastructure.
- Identity and access management: The ability to manage user access to systems and resources within an organization’s IT infrastructure.
- Network security monitoring: The ability to monitor network activity and identify potential security threats.
- Endpoint security: The ability to monitor and protect endpoint devices, such as servers and workstations.
- Application security: The ability to monitor and protect applications and application servers.
- Cloud security: The ability to monitor and protect cloud-based systems and resources.
- Data protection: The ability to protect data from unauthorized access or tampering.
- Mobile device management: The ability to manage and secure mobile devices that are connected to the organization’s IT infrastructure.
- Insider threat detection: The ability to identify potential insider threats and unusual patterns of behavior by employees or contractors.
- Intrusion detection and prevention: The ability to identify and prevent potential security breaches.
- Data loss prevention: The ability to prevent the unauthorized exfiltration of data from an organization’s IT infrastructure.
- Integration with third-party tools: The ability to integrate with other security tools and systems.
- Custom reporting: The ability to create custom reports and dashboards to meet the specific needs of an organization.
How do you build a SIEM use case?
To build a SIEM (Security Information and Event Management) use case, you will need to follow these steps:
- Identify the security objectives: Determine the security goals that you want to achieve with your SIEM, such as detecting and responding to threats, compliance, or incident response.
- Assess your current security posture: Conduct an assessment of your current security posture to identify any gaps or weaknesses that the SIEM can help address.
- Gather and analyze data: Collect data from the systems and devices on your network, and analyze it to identify patterns and trends that may indicate potential security threats.
- Define the use case: Based on the data you have collected and analyzed, define the specific security scenario that you want to address with your SIEM.
- Design the solution: Develop a plan for how the Security Information and Event Management will be used to address the security scenario you have defined. This may include configuring data collection, defining rules and policies, and integrating with other security tools and systems.
- Test and validate: Test the SIEM to ensure that it is correctly identifying and flagging relevant events, and validate the results to ensure that the SIEM is functioning as intended.
- Monitor and maintain: Ongoing monitoring and maintenance is important to ensure that the Security Information and Event Management remains effective over time. This may include adjusting rules and policies as needed, and testing and validating the Security Information and Event Management on a regular basis.
Is Splunk the best SIEM?
Splunk may not be the “best” SIEM (Security Information and Event Management) solution, as various organizations may have quite varied requirements and preferences. Splunk is a well-known and popular platform for Security Information and Event Management, and it provides a number of features and capabilities that can be appealing to some enterprises.
When selecting a SIEM, it is crucial to carefully assess the unique demands and requirements of your organization and to take into account a variety of possibilities.
When assessing Security Information and Event Management solutions, you may wish to take into account a number of criteria, such as:
- Scalability: Does the SIEM scale to meet the needs of your organization as it grows?
- Integration: Can the Security Information and Event Management integrate with other tools and systems that you use in your environment?
- Usability: Is the SIEM easy to use and understand for your security team?
- Cost: Does the Security Information and Event Management fit within your budget?
- Support: Does the SIEM vendor offer adequate support and resources to help you get the most out of the product?
You may decide which Security Information and Event Management system is the best fit for your firm by taking into account these and other considerations.
How to choose a SIEM solution?
When selecting a SIEM (Security Information and Event Management) solution, take into account the following factors:
- Scalability: Does the SIEM scale to meet the needs of your organization as it grows?
- Integration: Can the Security Information and Event Management integrate with other tools and systems that you use in your environment?
- Usability: Is the SIEM easy to use and understand for your security team?
- Cost: Does the Security Information and Event Management fit within your budget?
- Support: Does the SIEM vendor offer adequate support and resources to help you get the most out of the product?
- Features and capabilities: Does the SIEM offer the features and capabilities that you need, such as event collection and aggregation, data normalization, event correlation, and rule-based alerting?
- Security: Is the SIEM itself secure and able to protect against potential threats?
- Reputation: What are the reputation of the Security Information and Event Management vendor and the product in the market?
You may decide which Security Information and Event Management system is the best fit for your firm by taking into account these and other considerations.
Before making a decision, you might also want to read customer evaluations and case studies and think about trying out several solutions through a trial or pilot program.
What is DEM in SIEM?
DEM often stands for “detection and event management” in the context of SIEM (Security Information and Event Management). This refers to the procedures and tools used by a security information and event management system to identify and handle security-related issues and occurrences.
This often contains functions like data normalization, event correlation, event collection and aggregation, and rule-based alerting. With the help of these functionalities, a SIEM is able to collect and examine log data as well as other security-related events from multiple sources inside the IT infrastructure of a business, looking for patterns and trends that could point to possible security concerns.
To assist security analysts in analyzing and responding to the danger, the SIEM can subsequently provide alerts or take other steps.
In general, DEM’s role in a security information and event management system is to assist companies in swiftly and effectively identifying and responding to potential security risks.
How to install a SIEM?
Here are the general steps for installing a SIEM (Security Information and Event Management) tool:
- Choose a SIEM solution: Research and compare different SIEM solutions to determine which one is the best fit for your organization’s needs and budget.
- Download and install the software: Follow the instructions provided by the Security Information and Event Management vendor to download and install the software on your server or another host machine.
- Configure data collection: Set up data collection agents or configure the systems and devices on your network to send their logs to the SIEM using Syslog or another method.
- Normalize log data: Use the SIEM’s log normalization capabilities to ensure that the logs from different sources are in a consistent format.
- Set up rules and policies: Define rules and policies in the Security Information and Event Management to specify which types of events should be flagged and how they should be handled.
- Test and validate: Test the SIEM to ensure that logs are being collected and processed correctly, and validate the results to ensure that the Security Information and Event Management is correctly identifying and flagging relevant events.
- Monitor and maintain: Ongoing monitoring and maintenance are important to ensure that the Security Information and Event Management remains effective over time. This may include adjusting rules and policies as needed and testing and validating the Security Information and Event Management on a regular basis.
There can be more processes or things to think about during the installation process, depending on the individual Security Information and Event Management system you select. To guarantee a successful installation, be sure to closely adhere to the directions given by the Security Information and Event Management vendor.

What elements would you typically expect to make up a security information and event management SIEM environment?
A security information and event management (SIEM) environment typically consists of the following elements:
- Data sources: These are the systems and devices that generate security-related events and log data that is collected by the Security Information and Event Management. Examples include servers, workstations, network devices, and applications.
- Data collection agents: These are software programs that are installed on the data sources to collect log data and send it to the Security Information and Event Management.
- SIEM server: This is the central server that runs the Security Information and Event Management software and processes the collected log data.
- SIEM database: This is a database that is used to store the collected log data and other information related to Security Information and Event Management.
- Rules and policies: These are the rules and policies that are defined in the Security Information and Event Management to specify which types of events should be flagged and how they should be handled.
- User interface: This is the interface that is used by security analysts to interact with Security Information and Event Management, view log data, create reports, and respond to security events.
- Integration with other tools and systems: The SIEM may also be integrated with other security tools and systems, such as vulnerability scanners, intrusion detection systems, and incident response platforms.
Overall, the goal of a SIEM environment is to provide a centralized view of security data from across an organization’s IT infrastructure and to help identify and respond to potential security threats.
Which SIEM function tries to tie events together?
Event correlation is a SIEM (Security Information and Event Management) function that aims to connect events. In order to spot patterns of activity and potential security concerns, event correlation analyses log data and other security-related events from many sources.
For instance, a SIEM may employ event correlation to find a pattern of login failures that are all coming from the same IP address if it is receiving logs from numerous servers and workstations. This might be a sign of a potential brute force attack, and the Security Information and Event Management could send out an alert or do other things to assist security analysts in analyzing and addressing the danger.
Overall, event correlation is a crucial component of SIEMs because it enables businesses to recognize and address possible security risks that may not be immediately evident when examining log data or events on their own.
Which feature provides SIEM greater visibility into the entire network?
Data gathering and aggregation is one function that can give SIEM (Security Information and Event Management) more insight throughout the entire network. With the help of this functionality, a SIEM can gather and aggregate security-related events and log information from numerous points inside the IT architecture of a business.
A SIEM might be set up to gather logs from servers, workstations, network devices, and apps, for instance. The SIEM can offer a more complete picture of activity throughout the entire network by gathering log data from these many sources. Security analysts may find it difficult to detect patterns of activity and potential security risks when examining log data from a single source.
Overall, data collection and aggregation is a crucial SIEM function since it gives businesses better network awareness and makes it easier to spot potential security issues.
SIEM & SOC
Security information and event management, or SIEM, and security operations centers, or SOCs, are two concepts with a lot in common.
A software platform known as security information and event management aids businesses in the detection, investigation, and reaction to possible security risks. In order to accomplish this, it gathers and examines log data as well as other security-related events from numerous sources within an organization’s IT infrastructure, utilizing rules and regulations to spot patterns of activity that could be signs of possible threats.
SOC, on the other hand, describes a group or organization that is in charge of overseeing and responding to security-related incidents. This may entail actions like keeping an eye on logs and alerts, looking into occurrences of security and responding to those incidents.
In actuality, SIEM and SOC frequently work hand in hand, with SIEM providing the tools and information that SOC needs to detect and respond to potential security risks.
Others may take a more distributed approach, with various teams or individuals using the Security Information and Event Management as part of their overall security responsibilities. Some organizations may have a dedicated SOC team that is responsible for using Security Information and Event Management to monitor and respond to security events.
How does security information and event management system SIEM in a SOC
A security information and event management (SIEM) system can play a number of important roles within a SOC (Security Operations Center). Some of the ways that a SIEM can be used within a SOC include:
- Event collection and aggregation: The SIEM can collect and combine security-related events and log data from various sources within an organization’s IT infrastructure, providing a centralized view of security data.
- Event correlation: The SIEM can use rules and policies to identify patterns of activity that may indicate potential security threats, and generate alerts or take other actions to help security analysts investigate and respond.
- Compliance reporting: The SIEM can generate reports to demonstrate compliance with various regulations and standards, helping the SOC ensure that the organization is meeting its legal and regulatory obligations.
- Threat intelligence integration: The SIEM can incorporate threat intelligence feeds and other sources of information to help the SOC identify potential threats.
- Security analytics: The SIEM can use machine learning algorithms and other techniques to analyze security data and identify patterns and trends that may indicate potential security threats.
- Forensics and investigation tools: The SIEM can provide tools and features to help security analysts investigate and respond to security events.
Overall, the goal of using Security Information and Event Management within a SOC is to help the organization detect and respond to potential security threats as quickly and effectively as possible.


Fairly certain he will have a good read. Thank you for sharing!