User and Entity Behavior Analytics is the abbreviation. It is a cybersecurity tool that analyses user and system behavior patterns using machine learning algorithms to spot odd or suspicious activities that could be a sign of a security problem. In order to establish a baseline of typical behavior, UEBA systems track user actions and behaviors, including login patterns, file access, and network traffic. After that, they employ this data to look for variations from the norm that can point to a security risk, such as a cyberattack or insider threat.
What is UEBA in SIEM?
A SIEM (Security Information and Event Management) system includes UEBA as a component. Network logs, firewall logs, and application logs are just a few of the logs that are monitored and analyzed by SIEM systems. Utilizing user and system behavior patterns for analysis, UE-BA seeks out anomalous or suspicious conduct that could be a sign of a security threat. SIEM solutions give enterprises a thorough understanding of their security posture by integrating UE-BA with other security technologies including intrusion detection and prevention systems (IDPS) and vulnerability scanners. This enables organizations to quickly identify and address security threats.
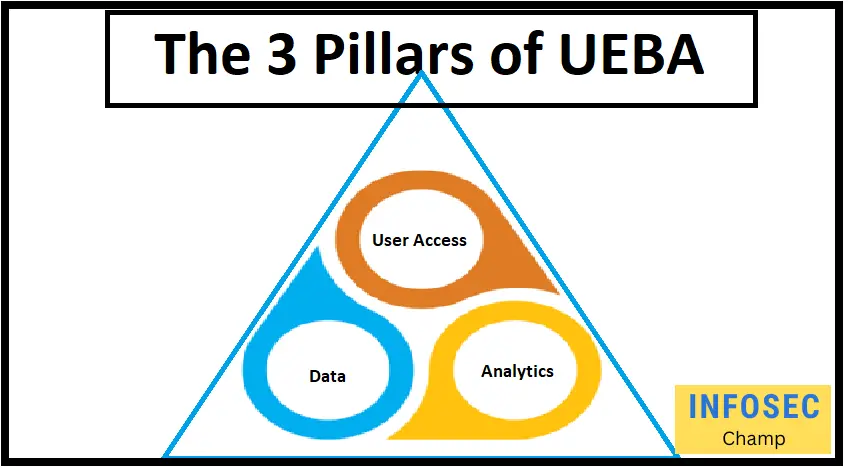
What are the three pillars of UEBA?
A UEBA system typically consists of a number of pillars or parts. These could consist of:
- Data gathering and analysis: UE-BA systems get information from a range of sources, including firewall logs, application logs, and network logs. Then, machine learning algorithms are used to examine this data in order to find patterns of typical activity and discover variations from these patterns that can point to a security problem.
- Contextual analysis: UE-BA systems frequently have contextual analysis features that let them consider the context of an event while deciding whether or not it is suspicious. For instance, viewing a sensitive file on a company-owned computer during business hours might not raise any red flags, but doing the same thing on a personal device or outside of regular business hours might.
- Threat intelligence and response: Threat intelligence feeds, which offer details about recognized security risks and vulnerabilities, are frequently included in UE-BA systems. The system uses this information to identify and rank possibly dangerous behavior. Systems for User and Entity Behavior Analytics might also provide incident response features, such as the capacity to notify security personnel or stop ominous conduct.
How does UEBA work?
Data is gathered by UEBA systems from a variety of sources, including firewall logs, application logs, and network logs. After that, machine learning techniques are used to examine this data in order to create a baseline for typical system and user behavior inside an organization.
Following the creation of the baseline, the User and Entity Activity Analytics system continuously examines user and system behavior and compares it to the baseline to find variations from the norm that can point to a security problem. Strange access patterns, unusual file access, or unexpected network traffic are a few examples of these aberrations.
The UE-BA system will create an alert or notification to notify security personnel when it discovers a deviation from the baseline that it deems suspicious. The system may also perform automated tasks like quarantining a suspicious file or denying access to a certain resource.
User and Entity Behavior Analytics continuously monitor user and system behavior and notify security staff of any unusual or suspect behavior in order to assist businesses in quickly identifying and responding to security threats.
Why is UEBA needed?
UEBA is required because conventional security tools like firewalls and antivirus software frequently fail to identify and address contemporary security threats. These dangers frequently include knowledgeable attackers who employ various strategies, like social engineering, to break into networks and steal confidential information.
By offering a more thorough picture of an organization’s security posture and assisting in the detection and mitigation of security threats that might not be obvious to conventional security solutions, User and Entity Behavior Analytics is created to address these issues.
UE-BA systems can assist companies in identifying and responding to security threats that could otherwise go unreported by continuously monitoring user and system behavior and using machine learning algorithms to recognize deviations from typical behavior. By doing this, firms can prevent data breaches and other security incidents and lessen the effects of any that do happen.
Can UEBA detect compromised accounts?
Yes, The answer is that UEBA systems are made to spot odd or suspicious behavior that might point to a security problem, like a compromised account. When an account is compromised, the attacker usually uses it to get access to resources or carry out deviant behaviors from the norm for that account.
These departures from the norm can be found by User and Entity Behavior Analytics systems, which can then provide an alert to inform security staff. The UE-BA system might flag these acts as suspicious and send out a warning, for instance, if an attacker enters into an account from a strange place or accesses a lot of files quickly.
User and Entity Behavior Analytics solutions can assist firms in identifying various security issues, such as insider threats, efforts at data exfiltration, and cyberattacks, in addition to compromised accounts.

How does UEBA matter for security?
UEBA is important for security because it gives a more complete picture of an organization’s security posture and makes it easier to identify and address security risks that conventional security technologies might miss.
UE-BA systems can assist companies in identifying and responding to security threats that could otherwise go unreported by continuously monitoring user and system behavior and using machine learning algorithms to recognize deviations from typical behavior. This can assist businesses in preventing data breaches and other security issues, as well as reducing the effects of any such incidents that do happen.
By offering insights into user and system behavior patterns, User and Entity Behavior Analytics solutions can assist organizations in optimizing their security efforts in addition to identifying security threats. Before they are used by attackers, this can assist organizations in identifying and addressing potential security flaws.
When was UEBA invented?
It is challenging to pinpoint the exact date that UEBA (User and Entity Behavior Analytics), a relatively new cybersecurity tool, was “developed.” The idea of utilizing machine learning algorithms to examine user and system behavior patterns to detect security risks has been around for even longer than the development of UEBA systems, which have been under development for a number of years.
The increasing complexity and sophistication of contemporary security threats, which traditional security technologies, like firewalls and antivirus software, are not always effective at detecting and responding to, has been the driving force behind the development of User and Entity Behavior Analytics systems. In order to provide a more thorough picture of an organization’s security posture and to identify and address dangers that conventional security technologies might not be able to see, UE-BA has emerged.
What are UEBA tools?
The purpose of UEBA (User and Entity Behavior Analytics) technologies is to study user and system behavior patterns in order to spot any odd or suspicious behavior that could be a symptom of a security concern. Tools for User and Entity Behavior Analytics are frequently employed as parts of a SIEM (Security Information and Event Management) system and are frequently utilized in enterprise-level systems to monitor and defend against security threats.
UE-BA tools, for instance, include:
- Splunk UBA: A UE-BA tool that analyses user and system behavior patterns using machine learning methods to spot odd or suspicious behavior.
- LogRhythm NextGen SIEM: A UEBA product that integrates User and Entity Behavior Analytics with additional security tools including intrusion detection and prevention systems (IDPS) and vulnerability scanners to give a thorough picture of an organization’s security posture.
- Exabeam User Activity Analytics: is a UEBA platform that analyses user and system behavior patterns using machine learning algorithms to spot security issues and offer incident response capabilities.
These are only a handful of the numerous tools for User and Entity Behavior Analytics that are offered on the market. Tools for User and Entity Behavior Analytics differ in terms of their features, capabilities, and cost, so it’s critical to thoroughly consider your alternatives to find the one that best meets your organization’s goals.
What is Log360 UEBA?
A cybersecurity technology called Log360 UE-BA (User and Entity Behavior Analytics) is used to find odd or suspicious activities that could be a sign of a security concern. It is a part of the Log360 security platform, which is an enterprise-level environment-specific security information and event management (SIEM) solution.
Log360 UE-BA analyses user and system behavior patterns using machine learning techniques to spot outliers that could be signs of a security concern. It can keep track of a wide range of data sources, including firewall logs, application logs, and network logs, and it can send alerts and notifications to security staff in the event of any odd or suspected behavior.
The Log360 platform contains various security technologies, such as intrusion detection and prevention systems (IDPS), vulnerability scanners, and endpoint protection, in addition to User and Entity Behavior Analytics, to give a complete picture of an organization’s security posture.
Explain SIEM, UEBA, and SOAR differences
Security technology known as SIEM (Security Information and Event Management) is used to track and examine information about security from a range of sources, including network logs, firewall logs, and application logs. SIEM systems are made to assist enterprises in quickly identifying and addressing security issues.
A SIEM system’s UEBA (User and Entity Behavior Analytics) component analyses user and system behavior patterns using machine learning algorithms to spot odd or suspicious activities that could be a sign of a security problem. Systems for tracking user activities and behaviors, such as login patterns, file access, and network traffic, are used to provide a baseline of typical activity. After that, they employ this data to look for variations from the norm that can point to a security risk, such as a cyberattack or insider threat.
A security solution called SOAR (Security Orchestration, Automation, and Response) is used to automate and streamline the process of identifying and responding to security threats. Security threats are identified and prioritized by SOAR systems using a combination of automation, analytics, and human expertise. SOAR systems may also coordinate the response to these threats across various security tools and systems. Organizations may speed up the time it takes to respond to security issues by using SOAR technologies to improve their incident response capabilities.
In general, SIEM, UEBA, and SOAR are all made to assist enterprises in identifying and counteracting security risks. They differ in terms of the particular data sources they monitor, the kinds of security risks they are designed to detect, and the particular response capabilities they offer, even though they have some similar goals and abilities.
UEBA for cyber security
A cybersecurity tool called UEBA (User and Entity Behavior Analytics) is used to find odd or suspicious activities that could be a sign of a security problem. It analyses user and system activity patterns using machine learning techniques to spot outliers that could be signs of a security concern.
In order to build a baseline of typical behavior, UEBA systems are used to monitor user actions and behaviors, such as login patterns, file access, and network traffic. After that, they employ this data to look for variations from the norm that can point to a security risk, such as a cyberattack or insider threat.
A SIEM (Security Information and Event Management) system, a type of security technology used to monitor and analyze security-related data from numerous sources, frequently uses UEBA as a component. SIEM systems offer a comprehensive view of an organization’s security posture and assist organizations in quickly identifying and responding to security threats by integrating User and Entity Behavior Analytics with other security technologies like intrusion detection and prevention systems (IDPS) and vulnerability scanners.
UEBA vs EDR
Cybersecurity tools like UEBA (User and Entity Behavior Analytics) and EDR (Endpoint Detection and Response) are used to identify and address security risks. However, they function at various places in the security architecture and are built to address various risks.
Machine learning algorithms are used by UEBA systems to study user and system behavior patterns in order to find odd or suspicious activities that could be a sign of a security concern. In order to establish a baseline of expected activity, they are frequently used to monitor network-level data, such as login patterns, file access, and network traffic. When building a SIEM (Security Information and Event Management) system, UE-BA systems are frequently employed as a component.
Contrarily, EDR systems are made to identify and react to security threats that have already made it to an organization’s endpoint devices, including laptops, servers, and mobile devices. EDR systems use machine learning techniques to identify suspicious behavior that can signal to a security problem while continuously monitoring endpoint activity. Additionally, they can offer incident response features including the ability to roll back malicious changes or isolate infected devices.
Overall, UEBA and EDR can be used in conjunction to create a comprehensive security plan because they are both crucial tools for spotting and addressing security issues.
When choosing which tools to utilize, it is crucial to be aware of each technology’s advantages and disadvantages as they each handle distinct risks and work at various points in the security architecture.

Top 10 UEBA solutions | UEBA Gartner ranking
The optimal UEBA (User and Entity Behavior Analytics) solution for a given business would rely on its individual needs and requirements. There are several UEBA (User and Entity Behavior Analytics) solutions available on the market. In light of this, the following list of 10 UE-BA solutions that are popular and well-liked in the sector:
- Splunk: A program that analyses user and system behavior patterns in order to find out-of-the-ordinary or suspicious activities.
- LogRhythm NextGen SIEM: A complete picture of an organization’s security posture is provided by LogRhythm NextGen SIEM, a solution that combines UE-BA with other security technologies like intrusion detection and prevention systems (IDPS) and vulnerability scanners.
- Exabeam User Behavior Analytics: Exabeam User Activity Analytics is a UE-BA solution that analyses user and system behavior patterns using machine learning algorithms to spot security vulnerabilities and offer incident response tools.
- Fortinet: The FortiSIEM platform includes a comprehensive security information and event management (SIEM) solution from Fortinet.
- Vectra Cognito: A program that analyses network traffic in real-time for security concerns and incident response tools using machine learning methods.
- Cybereason EDR: A tool for detecting and responding to security threats that combines UE-BA and endpoint detection and response (EDR) capabilities.
- LogPoint: A program that analyses user and system behavior patterns using machine learning techniques in order to spot anomalous or suspicious activities and offer incident response capabilities.
- Darktrace: A program that analyses network traffic in real-time using machine learning algorithms to spot security issues and offer incident response tools.
- Microsoft UE-BA and incident response automation are combined in a Mircosoft solution to assist businesses in quickly identifying and addressing security issues.
- Forcepoint: A program that analyses user and system behavior patterns using machine learning techniques in order to spot anomalous or suspicious activities and offer incident response capabilities.
These are but a few of the numerous UE-BA solutions that are offered in the market. In order to choose the UE-BA solution that best meets your organization’s goals, it is crucial to thoroughly consider the features, capabilities, and pricing of each choice.
UEBA Fortinet
One of the cybersecurity solutions offered by Fortinet is the UEBA (User and Entity Behavior Analytics) tool. The UE-BA tool from Fortinet is a component of the FortiSIEM platform, a complete security information, and event management (SIEM) system.
The UEBA solution from Fortinet analyses user and system behavior patterns using machine learning algorithms to spot odd or suspicious activities that could be a sign of a security issue. It can keep track of a wide range of data sources, including firewall logs, application logs, and network logs, and it can send alerts and notifications to security staff in the event of any odd or suspected behavior.
For a complete picture of an organization’s security posture, the FortiSIEM platform also offers other security technologies like intrusion detection and prevention systems (IDPS), vulnerability scanners, and endpoint protection in addition to UEBA. The UE-BA solution from Fortinet is made for enterprise-level environments and is meant to assist businesses in quickly identifying and responding to security threats.
UEBA Splunk
A UEBA (User and Entity Behavior Analytics) solution called Splunk UBA (User Behavior Analytics) is created to assist enterprises in identifying and addressing security issues. It is a part of the comprehensive security information and event management (SIEM) platform provided by Splunk Enterprise.
Splunk UBA analyses user and system behavior patterns using machine learning algorithms to find odd or suspicious activities that can point to a security vulnerability. It can keep track of a wide range of data sources, including firewall logs, application logs, and network logs, and it can send alerts and notifications to security staff in the event of any odd or suspected behavior.
The Splunk Enterprise security platform offers a holistic view of an organization’s security posture in addition to UE-BA by integrating additional security technologies, such as intrusion detection and prevention systems (IDPS) and vulnerability scanners. Splunk UBA is meant to assist enterprises in quickly identifying and responding to security risks. It is made for enterprise-level environments.
UEBA ManageEngine
A product called UE-BA (User and Entity Behavior Analytics) is offered by ManageEngine, a provider of IT management and security solutions. The Security Manager Plus UEBA tool from ManageEngine is a part of the ManageEngine Log360 platform, a complete security information, and event management (SIEM) solution.
Security Manager Plus analyses user and system behavior patterns using machine learning techniques to find odd or suspicious activities that can point to a security concern. It can keep track of a wide range of data sources, including firewall logs, application logs, and network logs, and it can send alerts and notifications to security staff in the event of any odd or suspected behavior.
To give a complete picture of an organization’s security posture, the ManageEngine Log360 platform also contains other security solutions, such as intrusion detection and prevention systems (IDPS), vulnerability scanners, and endpoint protection. The purpose of Security Manager Plus, which is created for enterprise-level environments, is to assist enterprises in quickly identifying and responding to security risks.
UEBA sentinel
One of the cybersecurity solutions offered by Sentinel is a technology called UEBA (User and Entity Behavior Analytics). Sentinel One UEBA, the company’s UE-BA tool, is a part of the Sentinel One Endpoint Protection Platform, an all-encompassing endpoint security solution.
Sentinel One UEBA analyses user and system behavior patterns using machine learning algorithms to find odd or suspicious activities that can point to a security concern. It can keep track of a wide range of data sources, including firewall logs, application logs, and network logs, and it can send alerts and notifications to security staff in the event of any odd or suspected behavior.
The Sentinel One Endpoint Protection Platform contains UE-BA in addition to other security tools like vulnerability scanners and intrusion detection and prevention systems (IDPS) to give a complete picture of an organization’s endpoint security posture. Sentinel One UEBA is made for enterprise-level environments and is meant to assist businesses in quickly identifying and addressing security risks.
UEBA exabeam
A cybersecurity technology called Exabeam User Behavior Analytics (UE-BA) is used to look for odd or suspicious activity that could be a sign of a security problem. It is a part of the complete security information and event management (SIEM) system known as the Exabeam Security Management Platform.
Exabeam UE-BA analyses user and system activity patterns using machine learning techniques to spot outliers that could be signs of a security concern. It can keep track of a wide range of data sources, including firewall logs, application logs, and network logs, and it can send alerts and notifications to security staff in the event of any odd or suspected behavior.
The Exabeam Security Management Platform contains UE-BA in addition to other security tools like vulnerability scanners and intrusion detection and prevention systems (IDPS) to give a complete picture of an organization’s security posture. Exabeam UE-BA is created for enterprise-level environments and is meant to assist businesses in quickly identifying and addressing security risks.
UEBA use cases
A cybersecurity tool called UEBA (User and Entity Behavior Analytics) is used to find odd or suspicious activities that could be a sign of a security problem. Machine learning techniques are used by UEBA systems to evaluate user and system activity patterns and spot outliers that could be signs of a security issue.
Here are some instances of typical UEBA use cases:
- Detecting insider threats: UEBA systems can monitor user behavior patterns, including file access and network traffic, to spot out-of-the-ordinary conduct that might point to an insider threat, such as a worker stealing confidential data.
- Detecting cyber attacks: UEBA systems can monitor network-level data, such as login patterns, and network traffic, to spot changes from the usual that might be signs of a cyber assault, like malware infection or a brute-force password attempt.
- Detecting data exfiltration attempts: UE-BA systems can monitor user behavior patterns, such as file access and network traffic, to spot out-of-the-ordinary behavior that may point to an effort to steal sensitive material. For example, they can spot an employee downloading a lot of data to a cloud storage service.
- Optimizing security efforts: UEBA systems can offer insights into user and system activity patterns that can assist companies in identifying and addressing potential security vulnerabilities before they are exploited by attackers. This helps to maximize security efforts.
10 Best practices for UEBA
UEBA (User and Entity Behavior Analytics) system implementation and maintenance best practices are as follows:
- Establish definite objectives and targets for your UEBA implementation. This will enable you to choose the most crucial behaviors to watch for and the proper warning thresholds.
- A baseline of typical behavior should be established for each person and entity in your system. You will be able to spot strange or suspicious activities more readily as a result.
- To present a more thorough picture of user and entity behavior, combine data from many sources. In addition to data from internal sources like threat intelligence feeds, this may also comprise data from servers, applications, and network devices.
- To help identify anomalous behavior and minimize the number of false positives, use machine learning techniques.
- To make sure your UEBA rules and levels are still applicable and useful, regularly evaluate and update them.
- Use various security layers to stave off threats that your UEBA system might not be able to identify.
- Real-time monitoring of user and entity behavior enables prompt threat detection and remediation.
- Establish a strong incident response strategy to make sure that any dangers are immediately and efficiently addressed.
- To make sure your UEBA system is operating as intended and to spot any areas for improvement, test and assess it frequently.
- To make sure that your system is as successful as possible, stay up to date with the most recent UEBA technology and best practices.