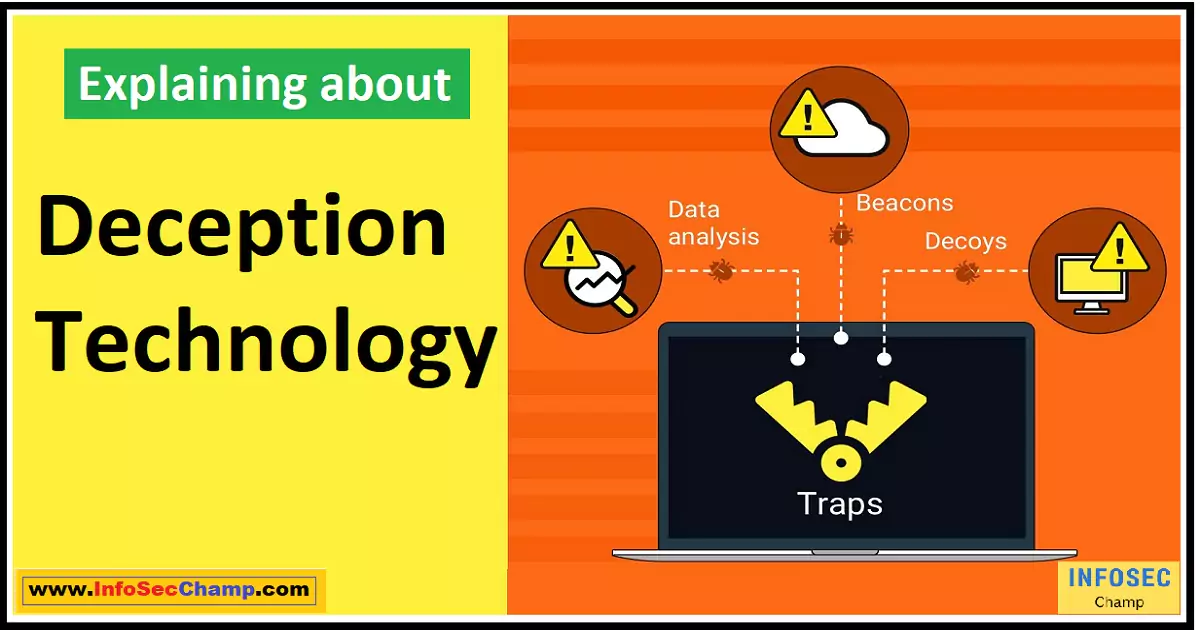
Shocking: 99% of Businesses Lack This Essential Deception Technology in 2023
In 2023, deception technology is absolutely critical for businesses and organizations hoping to protect themselves from the growing threat of cyber attacks. With data breaches now costing companies an average of $4.35 million per incident, and global cybercrime damages set to hit $10.5 trillion annually by 2025, the stakes have never been higher. The good news? … Read more