A user can access different applications using a single set of login credentials thanks to the authentication method known as single sign-on (SSO) (username and password). A user only needs to log in once to access numerous systems or apps using single sign-on, as opposed to being requested to do so at each location. Minimizing the number of locations where login credentials need to be kept and handled, can both make it simpler for users to access the resources they require and improve security. The use of a central authentication service, a federation of identity systems, or other techniques are just a few of the ways single sign-on can be done.
What is SSO and How Does it work?
A user can access different applications using a single set of login credentials thanks to the authentication technique known as single sign-on (SSO) (username and password). When a person uses Single Sign-On, a central authentication service authenticates them, enabling them to access various systems or apps without having to log in again at each one.
Here’s an illustration of how SSO could function:
- Upon arriving at a website or application, a user selects the “login” button.
- The user enters their login information on the SSO login screen after being forwarded there (username and password).
- A secure token that symbolizes the user’s authorized session is created by the SSO authentication service once it has verified the user’s credentials and determined if they are legitimate.
- The user is then forwarded back to the original website or application, which relies on the single sign-on service and grants access to its resources in accordance with the security token obtained.
- The user will no longer be required to log in again in order to access other systems or applications that have been set up to trust the Single Sign-On service.
Single Sign-On may, in general, make it simpler for users to access the resources they require while also enhancing security by minimizing the number of locations where login credentials must be kept and handled.
Why SSO is important?
Single Sign-On (SSO) may be crucial for the following reasons:
- Convenience: By enabling users to log into various systems or apps using a single set of login credentials, SSO can make it simpler for users to access the resources they require. Users won’t have to remember and enter different login credentials for each program they use, which can save time and ease annoyance.
- Improved security: SSO can increase security by cutting down on the number of locations where login credentials must be kept and managed. A single set of login credentials is all that users need to remember with SSO, which can lower the risk of password-related security breaches.
- Enhanced user experience: Single Sign-On can enhance the user experience by lowering the number of login prompts users must navigate through and by making it simpler for users to access the resources they require.
- Simplified IT management: Single Sign-On can reduce the number of separate authentication systems that need to be managed and integrated.
Overall, Single Sign-On can benefit both users and IT specialists by facilitating resource access, strengthening security, and upgrading the user experience.
How do I access single sign-on?
Depending on how Single Sign-On (SSO) is implemented in your company, there are a number of different ways to access it. Here are a few illustrations:
- Through a central authentication service: To administer SSO, many organizations make use of a central authentication service, such as Okta or OneLogin. In this scenario, users can access SSO by logging into the website or application of the central authentication service.
- Through a federation of identity systems: To control SSO, some businesses employ an identity federation, such as SAML or OpenID Connect. In this instance, users can access Single Sign-On by logging into one of the federated identity systems.
- Through a specific application or website: Users can access SSO by logging in to the particular application or website because some programs or websites may offer their own Single Sign-On capability.
Overall, how SSO is deployed in your business will determine the precise methods to access it. You can try contacting your IT department or the support staff for the program or website you’re attempting to access if you’re unsure how to access SSO. They ought to be able to give you more details about how to access SSO.
What is the main advantage of single sign-on?
SSO’s primary benefit is that it enables users to log into various systems or apps with just one set of login information. Users may find this handier as they no longer need to remember and enter unique login information for each program they use. By minimizing the number of locations where login credentials need to be kept and handled, Single Sign-On can also increase security.
Users just need to remember one set of login information, which can lower the risk of password-related security breaches. By making it simpler for users to access the resources they require and lowering the number of login prompts they face, SSO can also improve the user experience. Last but not least, Single Sign-On can make IT management easier by minimizing the number of different authentication systems that need to be kept up-to-date and connected.

Advantages and disadvantages of single sign-on
The following are the advantages of single sign-on (SSO):
- Convenience: SSO makes it possible for users to log into various apps or systems using a single set of login information, which can save time and ease annoyance.
- Improved security: SSO can increase security by cutting down on the number of locations where login credentials must be kept and managed. Password-related security breaches may become less likely as a result.
- Enhanced user experience: SSO can improve user experience by making it simpler for users to access the resources they require and by lowering the number of login prompts they must deal with.
- Simplified IT management: Single Sign-On can reduce the number of separate authentication systems that need to be managed and integrated.
The following are some possible disadvantages of SSO:
- Dependence on a single system: Users won’t be able to access any of the systems or applications if the Single Sign-On system fails.
- Increased complexity: heightened complexity Single Sign-On can be more difficult to implement and maintain than maintaining individual authentication systems for every application.
- Potential security vulnerabilities: Potentially dangerous security flaws The security of all the systems and apps that rely on the Single Sign-On system could possibly be compromised if it is improperly configured or compromised.
- Lack of flexibility: SSO may not function properly with some systems or applications that have special authentication needs of their own.
What are the pros and cons of SSO?
Here are 20 advantages and disadvantages of single sign-on (SSO):
Pros:
- Convenience: SSO makes it simple for users to log into various systems or applications with only one set of login information.
- Improved security: By reducing the number of locations where login credentials must be saved and managed, SSO can lower the risk of security breaches linked to passwords.
- Enhanced user experience: Single Sign-On minimizes the number of login prompts users to receive and makes it simpler for them to access the services they require.
- Simplified IT management: Reduced amount of distinct authentication systems that need to be maintained and integrated thanks to Single Sign-On.
- Improved productivity: By eliminating the need for users to remember and enter numerous sets of login credentials, single sign-on can save users time and increase productivity.
- Enhanced security: Single Sign-On can increase security by enabling multifactor authentication and enabling enterprises to implement stricter password regulations.
- Improved compliance: By offering a central location to control and track user access, SSO can assist enterprises in meeting compliance obligations.
- Reduced IT costs: By removing the need to maintain different authentication systems, SSO can lower IT expenditures.
- Improved user adoption: SSO can increase user acceptance of new applications and systems by making it simpler for users to access them.
- Increased scalability: As an organization grows, SSO can make it simpler to scale access to systems and applications.
Cons:
- Dependency on a single system: Users won’t be able to access any of the systems or applications if the Single Sign-On system fails.
- Increased complexity: Compared to managing separate authentication systems for each application, implementing and administering Single Sign-On can be more challenging.
- Potential security vulnerabilities: The security of all systems and applications that rely on the Single Sign-On system may be jeopardized if it is improperly configured or compromised.
- Lack of flexibility: SSO may not function properly with some systems or applications that have special authentication needs of their own.
- Increased upfront costs: Implementing single sign-on may necessitate paying up ahead for items like software licenses and training.
- Compatibility issues: SSO may not function properly with outdated software or programs that aren’t built to support it.
- Limited customization: SSO may not allow for as much customization as independent authentication solutions.
- Increased integration efforts: Increased integration efforts may be necessary to make sure that SSO is compatible with all systems and apps.
- User frustration: Users may feel frustrated and less likely to use Single Sign-On if they experience problems with it.
- Increased reliance on IT: If IT resources are few, organizations may be forced to rely more on IT to operate and maintain the Single Sign-On system.
What are the benefits of single sign-on?
Single Sign-On (SSO) can offer the following security advantages:
- Reduced risk of password-related security breaches: By only requiring users to remember one set of login information, this technology can help to lower the chance of password-related security issues.
- Improved password security: Strengthened password policies, such as those that demand longer or more complicated passwords, can be enforced by businesses with the help of SSO, which can help to increase security.
- Enhanced security through multifactor authentication: Multifactor authentication improves security by requiring users to give additional authentication factors beyond just a username and password. SSO can enable multifactor authentication. By making it more difficult for unauthorized individuals to access systems and applications, can increase security.
- Centralized control over user access: SSO offers a central location to manage and track user access, which can enhance security by enabling companies to more easily monitor and regulate who has access to what resources. Centralized management over user access.
- Simplified compliance: By offering a central location to control and track user access, SSO can assist firms in complying with regulatory requirements.
By lowering the possibility of password-related security breaches, enhancing password security, enabling multifactor authentication, offering centralized control over user access, and streamlining compliance, single sign-on can generally offer a variety of security benefits of single sign on.
What are some of the risks of using single sign-on?
The following concerns should be taken into account while adopting Single Sign-On (SSO):
- Dependency on a single system: Users won’t be able to access any of the systems or applications if the SSO system fails. This may interfere with production and cause disruptions.
- Security vulnerabilities: If the SSO system is improperly set up or is compromised, it may jeopardize the safety of all the applications and systems that depend on it.
- Lack of adaptability: SSO may not function properly with some systems or applications that have special authentication needs of their own.
- Compatibility problems: SSO may not function properly with outdated software or programs that aren’t built to support it.
- User frustration: Users may feel frustrated and less likely to use Single Sign-On if they experience problems with it.
- Increased dependency on IT: If IT resources are few, organizations may be forced to rely more on IT to operate and maintain the Single Sign-On system.
- Increased complexity: Compared to managing separate authentication systems for each application, implementing and administering Single Sign-On can be more challenging.
- Increased upfront costs: An increase in up-front costs may be associated with the implementation of SSO, including those associated with software licenses and training.
- Limited customization: SSO may not allow for as much customization as independent authentication solutions.
Increased integration efforts: Increased integration efforts may be necessary to make sure that SSO is compatible with all systems and apps.
In order to minimize these dangers, it is crucial to carefully weigh the risks associated with implementing Single Sign-On and to make sure that the system is set up and secured correctly.
What is considered a drawback to single sign-on?
Using Single Sign-On (SSO) could have a number of disadvantages.
- Dependency on a single system: Users won’t be able to access any of the systems or applications if the SSO system fails. This may interfere with production and cause disruptions.
- Security vulnerabilities: If the SSO system is improperly set up or is compromised, it may jeopardize the safety of all the applications and systems that depend on it.
- Lack of flexibility: SSO may not function properly with some systems or applications that have special authentication needs of their own.
- Compatibility problems: SSO may not function properly with outdated software or programs that aren’t built to support it.
- User frustration: Users may feel frustrated and less likely to use Single Sign-On if they experience problems with it.
- Increased dependency on IT: If IT resources are few, organizations may be forced to rely more on IT to operate and maintain the Single Sign-On system.
- Increased complexity: Compared to managing separate authentication systems for each application, implementing and administering Single Sign-On can be more challenging.
- Increased upfront costs: An increase in up-front costs may be associated with the implementation of SSO, including those associated with software licenses and training.
- Limited customization: SSO may not allow for as much customization as independent authentication solutions.
- Increased integration efforts: Increased integration efforts may be necessary to make sure that SSO is compatible with all systems and apps.
In order to minimize these risks, it is crucial to carefully weigh the potential negatives of adopting Single Sign-On and to make sure that the system is correctly set up and secured.
Which protocol is used for single sign-on?
Numerous protocols are available for Single Sign-On (SSO). Here are a few illustrations:
- Security Assertion Markup Language (SAML): An established mechanism for communicating authentication and permission information across systems is Security Assertion Markup Language (SAML). It enables users to log in to one system—like the internal network of a business—and then access different systems—like cloud-based applications—without having to do so again.
- OpenID Connect: OAuth 2.0 is the foundation upon which the OpenID Connect protocol for user authentication is constructed. It enables users to sign in to one system (like a social media platform) and then access other systems that rely on the authentication of the first system (such as a cloud-based application).
- LDAP: A protocol for managing and accessing directory services, such as those required to store user authentication data, is called LDAP, or Lightweight Directory Access Protocol. It can be used to authenticate users and grant access to several systems as a component of a Single Sign-On solution.
- Kerberos: A user can log into one system and utilize Kerberos, a network authentication protocol, to access other systems connected to the same network without having to log in again. It frequently serves as Single Sign-On in business situations.
In general, the protocol chosen for SSO will rely on the unique demands and specifications of the company.
Are LDAP and SSO the same?
The Lightweight Directory Access Protocol (LDAP) is a protocol for managing and accessing directory services, such as those used to store user authentication data. A user can access various systems or apps using the single sign-on (SSO) authentication approach.
Although LDAP can be used as an SSO solution to authenticate users and grant access to various systems, SSO and LDAP are not the same things. Single Sign-On is an authentication technique, whereas LDAP is a protocol for accessing directory services. Single Sign-On can be implemented by combining LDAP with other technologies like SAML or Kerberos. SSO-unrelated uses of LDAP include directory-based authentication and authorization.
What tools are used to implement SSO?
There are numerous tools available for Single Sign-On implementation (SSO). Here are a few illustrations:
- Centralized authentication services: To administer single sign-on, many firms employ a central authentication service like Okta or OneLogin. For the purpose of controlling and authenticating user access to various systems and applications, these services offer a consolidated platform.
- Identity federation systems: Systems for managing SSO using an identity federation: SAML or OpenID Connect are two examples of identity federation systems. With these systems, users can sign in to one system (like a social media platform) and then access other systems that accept the authentication from the first system (such as a cloud-based application).
- Lightweight Directory Access Protocol (LDAP) servers: As part of an SSO solution, user authentication data can be stored and managed on LDAP servers. For Single Sign-On, LDAP servers can be used with other systems like Kerberos or RADIUS.
The specific technologies used to execute Single Sign-On will, in general, rely on the unique demands and requirements of the company. It is crucial to carefully weigh your alternatives and select technologies that are appropriate for the needs and available resources of your organization.
How to Implement Single Sign-On? | How does SSO Implementation Work?
The general procedures for implementing Single Sign-On (SSO) are as follows:
- List the applications and systems that will be a part of the single sign-on solution. This could apply to both internal and external systems, such as cloud-based or internal apps and systems.
- Select the authentication technique to be used for Single Sign-On. This could be a federation of identity systems like SAML or OpenID Connect, a central authentication service like Okta or OneLogin, or another approach like LDAP or Kerberos.
- Set up the systems and programs that will be a part of the single sign-on solution to trust the selected authentication technique. On each machine or application, this can entail installing software or making configuration adjustments.
- Configure the selected authentication mechanism to control user access to the SSO solution’s systems and applications after setting it up. This could entail setting up servers, modifying user permissions and accounts, and building trust between the systems and apps.
- Check the SSO solution’s functionality and the users’ access to the necessary systems and applications.
- Provide support as necessary and instruct users on how to utilize the single sign-on solution.
- To maintain security and make sure the Single Sign-On solution continues to suit the needs of the organization, monitor it and make any necessary upgrades or adjustments.
In order to ensure that Single Sign-On is configured appropriately and fits the goals of the organization, extensive planning and cooperation are needed before implementation.
20 steps to Implement Single Sign-On
The following 20 steps will help you establish Single Sign-On (SSO):
- Identify the applications and systems that will be a part of the SSO solution.
- Decide which user groups will be a part of the SSO solution.
- Identify the SSO authentication strategy that will be utilized.
- The infrastructure requirements for the selected authentication mechanism should be determined.
- Create the infrastructure required for the selected authentication technique.
- Set up the systems and programs that will be a part of the single sign-on solution to trust the selected authentication technique.
- Configure the selected authentication mechanism to control user access to the SSO solution’s systems and applications after setting it up.
- Create trusting connections between the applications and systems that are a part of the single sign-on solution.
- For the systems and apps covered by the single sign-on solution, configure user accounts and permissions.
- To make sure the SSO solution is operating properly, test it out.
- The Single Sign-On solution should be explained to users.
- Create a procedure for adding and removing applications and systems from the SSO solution.
- Create a procedure for including and deleting users from the SSO solution.
- Establish a procedure for controlling user access to the programs and systems covered by the SSO solution.
- Create a procedure for maintaining and monitoring the SSO solution.
- Create a strategy for handling probable Single Sign-On problems or failures.
- Put security measures in place to safeguard the SSO solution.
- As required, integrate the SSO solution with additional IT systems and procedures.
- Verify how SSO is being used.
- Check the SSO solution’s efficiency
What are the access control requirements for SSO?
When adopting Single Sign-On (SSO), there are a number of access control needs that should be taken into account:
- Authentication: Before being allowed access to the Single Sign-On solution, users should be required to provide their own authentication. This could entail employing multifactor authentication or another authentication method, such as giving a username and password.
- Authorization: The SSO solution should be set up such that users can access the systems and applications they are permitted to use while preventing them from using those that they are not. Creating user groups and giving those groups permission may be necessary for this.
- User management: The SSO solution must include a procedure for adding and deleting users as well as for controlling user access to systems and applications. This can entail managing user data by using a central directory service or another solution.
- Access control lists: ACLs, which define which users or groups are permitted access to which systems and applications, should be able to be defined as part of the SSO solution.
- Auditing: The SSO solution should offer a method for tracking successful and unsuccessful login attempts as well as auditing user access to systems and applications.
- Password policies: Strong password policies should be enforced by the SSO solution to guarantee the security of user accounts. This can entail setting minimum standards for password complexity and length.
All things considered, it’s crucial to carefully analyze the access control requirements of the Single Sign-On solution and to make sure that the right safeguards are in place to manage and protect user access to systems and applications.
What are LDAP and SAML?
The Lightweight Directory Access Protocol (LDAP) is a protocol for managing and accessing directory services, such as those used to store user authentication data. Users can be authenticated using LDAP, which can also be used to control access to applications and systems. It is a widely used protocol that is supported by a wide range of systems and applications.
A protocol called Security Assertion Markup Language (SAML) is used to exchange authentication and authorization information across computers. SAML enables a user to check in to one system (like a company’s internal network) and then access other systems (like cloud-based services) without having to log in again. Single Sign-On (SSO) features are frequently provided via SAML.
In general, SAML is a protocol for sharing authentication and authorization information across systems, whereas LDAP is a standard for administering directory services. To offer convenient and safe access to systems and applications, single sign-on solutions can use both LDAP and SAML.
What is the difference between SAML and SSO?
With the use of the Single Sign-On (SSO) authentication technique, a user can log into numerous systems and apps using just one set of login information. System-to-system data exchange for authentication and authorization is facilitated by the SAML protocol (Security Assertion Markup Language).
SAML can be used to achieve SSO by enabling a user to log in to one system (such as an organization’s internal network) and then access other systems (such as cloud-based applications) without the need to log in again. By enabling users to authenticate only once and access various systems without the need to authenticate again, SAML serves as a tool for attaining Single Sign-On.
SSO, however, extends beyond SAML alone. In addition to these, OpenID Connect, Kerberos, and LDAP are other protocols and technologies that can be applied to SSO.
Overall, Single Sign-On is an authentication solution that enables users to access different systems or apps with a single set of login credentials while SAML is a protocol for communicating authentication and authorization information between systems. Single Sign-On (SSO) can be accomplished with SAML, but it is not the only method.
What is the difference between SAML and OAuth?
Although OAuth and Security Assertion Markup Language (SAML) are both standards for exchanging authentication and authorization data, they are utilized for various reasons and function in various ways.
- A protocol called SAML is used to transfer authentication and authorization information across systems. It enables users to log in to one system—like the internal network of a business—and then access different systems—like cloud-based applications—without having to do so again. Single Sign-On (SSO) features are frequently offered via SAML.
- Not for authentication, OAuth is a standard for permission. OAuth is used to enable secure and convenient access to useful resources by one system (like a social networking platform) for another system (like a cloud-based application). OAuth presumes that the user has previously been authenticated by the system that stores the user resources rather than handling authentication itself.
In general, SAML and OAuth vary primarily in that SAML is used for both authentication and authorization while OAuth is just used for authorization. OAuth is used to enable one system to access user resources on another system, whereas SAML is frequently used for single sign-on.
Why use SAML for SSO?
Organizations may decide to adopt Security Assertion Markup Language (SAML) for Single Sign-On (SSO) for a number of reasons, including the following:
- Widely used and supported: SAML is a well-known protocol that is supported by a wide range of applications and systems. Because Single Sign-On solutions need to support a lot of systems, this makes it simple to interface with a variety of systems and applications.
- Secure: To guarantee the security of the authentication and authorization data that is sent between systems, SAML uses digital signatures and encryption. This makes user credentials secure and helps guard against unlawful access.
- User-friendly: SAML is user-friendly because it enables users to sign in to one system (like the internal network of a corporation) and then access other systems (like cloud-based services) without having to do so again. The user experience is seamless and practical as a result.
- Scalable: SAML is excellent for businesses with a large number of users and systems because it is built to enable large-scale deployments.
- Flexible: SAML is adaptable enough to satisfy the needs of many different businesses because it supports a wide range of authentication techniques, such as username and password, multifactor authentication, and others.
Overall, Single Sign-On systems can benefit from using SAML because it is a widely accepted, safe, and user-friendly protocol. It is a well-liked option for businesses that must offer convenient and safe access to lots of different systems and apps.
What is SSO id? | Why it is required?
An SSO system’s single Sign-On (SSO) ID is a special identification that is used to verify a user’s identity. In the Single Sign-On system, it is often a username or other identifier that is connected to the user’s account.
Since the SSO ID is needed to identify the user and verify their access to the systems and applications that are part of the SSO solution, it is necessary. The user would have to log into each system and application separately without an SSO ID, which would be difficult and possibly unsafe.
Overall, the SSO ID is a crucial component of an SSO system since it enables users to log into various systems and programmes using only one set of login information, offering a simple and safe method to control user access.
Single sign-on example
Here is an example of how Single Sign-On (SSO) may function in a professional environment:
- A user makes an initial attempt to use a cloud-based HR program.
- The user is forwarded to the company’s main Single Sign-On login page by the HR application.
- On the login screen, the user enters their SSO login information (username and password).
- The user’s credentials are verified by the SSO system, which subsequently enables them access to the HR application.
- The user has successfully logged in and can now access the resources and features they are permitted to utilize in the HR application.
- A project management tool, for example, is an alternative cloud-based program that the user wants to access.
- The company’s SSO system is trusted by the project management tool, which permits the user to access the program without having to log in again.
- The user has successfully logged in and may now access the resources and features they are permitted to use in the project management tool.
In this case, the Single Sign-On system enables the user to sign in to several cloud-based services using a single set of login information. This offers a simple and safe approach to controlling user access to several systems and programs.
How to enable single sign-on?
In order to enable Single Sign-On (SSO), you must take the following actions:
- Identify the applications and systems that will be a part of the SSO solution. This could apply to both internal and external systems, such as cloud-based or internal apps and systems.
- Identify the SSO authentication strategy that will be utilized. This could be a federation of identity systems like SAML or OpenID Connect, a central authentication service like Okta or OneLogin, or another approach like LDAP or Kerberos.
- Set up the SSO solution’s integrated systems and programs to trust the chosen authentication strategy. On each machine or application, this can entail installing software or making configuration adjustments.
- Configure the selected authentication mechanism to control user access to the SSO solution’s systems and applications after setting it up. This could entail setting up servers, modifying user permissions and accounts, and building trust between the systems and apps.
- Check the SSO solution’s functionality and the users’ access to the necessary systems and applications.
teach customers how to use the SSO system, and offer assistance as required. - To maintain security and make sure the SSO solution is still meeting the needs of the organization, monitor it and make any necessary upgrades or adjustments.
Overall, to guarantee that SSO is configured effectively and satisfies the goals of the company, careful planning and cooperation are required. In order to ensure that the SSO solution is functional, it is crucial to configure and secure it effectively and to choose an authentication mechanism that is appropriate for the organization’s needs and resources.

20 Best practices of Single Sign-On (SSO) Solutions
20 best practices for setting up and running a single sign-on (SSO) solution are listed below:
- List the applications and systems that will be a part of the single sign-on solution.
- Select the authentication technique to be used for Single Sign-On.
- Set up the systems and programs that will be a part of the single sign-on solution to trust the selected authentication technique.
- Configure the selected authentication mechanism to control user access to the systems and apps covered by the Single Sign-On solution. Set up the chosen authentication method.
- Check the SSO solution’s functionality and the users’ access to the necessary systems and applications.
- Provide support as necessary and instruct users on how to utilize the single sign-on solution.
- To maintain security and make sure the Single Sign-On solution continues to suit the needs of the organization, monitor it and make any necessary upgrades or adjustments.
- All user accounts should have strong passwords.
- All users should have multifactor authentication (MFA) enabled.
- User permissions should be regularly reviewed and updated to make sure they are appropriate.
- Track login activity and alert the authorities to any strange or suspected activities.
- Use SSL/TLS and other secure communication protocols to safeguard the transmission of sensitive data (for data security).
- By teaching users how to spot and prevent these kinds of assaults, you can defend against phishing attacks.
- Patch and upgrade systems and programs frequently to ward off vulnerabilities.
- Install security measures like firewalls and intrusion detection systems to prevent unwanted access to systems and applications (or Web Application Firewall).
- Review and revise security guidelines on a regular basis.
- To handle security events and breaches, establish a process.
- Make sure the SSO solution complies with all applicable rules, laws, and standards.
- To guarantee that the Single Sign-On solution is accessible in the event of an outage or other disturbance, implement a disaster recovery plan.
- Make sure the single sign-on solution is consistently reviewed and evaluated for efficacy to make sure it is fulfilling the needs of the organization.
Overall, following these best practices can help guarantee the effectiveness, efficiency, and security of an SSO solution.
Single sign-on google
With the use of Google’s Single Sign-On (SSO) service, users may log into different Google products and services using just one set of login information. This includes programs like Gmail, Drive, Calendar, and others from Google.
You must create a Google account and log in with it to the numerous Google services and applications you wish to access in order to use Google’s SSO service. You won’t have to log in again to use all of the programs and services to which you have been given access once you are signed into your Google account.
Organizations and individuals can both use Google’s SSO service. Google provides the Google Workspace suite to businesses, which consists of a number of productivity and collaboration applications in addition to Single Sign-On and other enterprise-level capabilities.
In general, Google’s SSO service offers customers a simple and safe way to use a single piece of login information to access different Google applications and services.
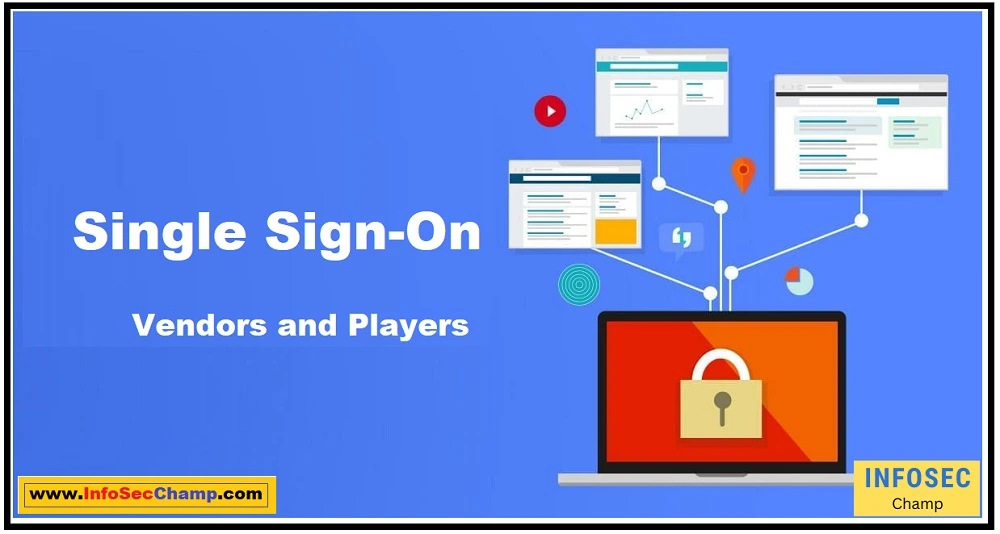
Top 15 Single Sign-On solutions
Here are 15 Single Sign-On (SSO) solutions:
- Okta
- OneLogin
- Microsoft Azure Active Directory
- Google Workspace
- Amazon Web Services (AWS) Single Sign-On
- Ping Identity
- Auth0
- Centrify
- Duo Security
- Saviynt
- SailPoint
- JumpCloud
- LastPass
- Bitium
- Freenome
User management, authentication, access control, and connectivity with numerous systems and apps are just a few of the capabilities and services that these SSO solutions offer. While some of these solutions are more general-purpose, others are targeted at certain sectors or use situations. It is crucial to carefully analyse your organization’s needs before choosing a single sign-on solution that will meet those demands.
What is a Single Sign-On error?
An issue that stops a user from accessing the systems and apps that are part of the SSO solution is known as a single sign-on (SSO) error. The cause of this can be an issue with the user’s login information, a configuration problem with the Single Sign-On solution, or a problem with the system or application being used.
Users may experience a number of typical SSO problems kinds, including:
- Incorrect login credentials: Errors with single sign-on are most frequently caused by incorrect login credentials. A user won’t be able to access the SSO solution if they enter the erroneous username or password.
- Expired or revoked credentials: Credentials that have expired or been revoked: Users whose credentials have expired or been revoked will not be able to access the Single Sign-On solution.
- Issues with configuration: If the SSO solution is improperly set up, users may be unable to access the systems and applications they require.
- System or application problems: Users may not be able to log in if the system or application being accessed is having problems.
It might be essential to troubleshoot the issue and ascertain the error’s cause in order to fix SSO issues. This could entail checking the user’s login information, confirming how the Single Sign-On solution is set up, or confirming the functionality of the system or application being accessed.
Single sign-on specification
A Single Sign-On (SSO) specification is a set of rules or specifications that describe the functionality and application of a Single Sign-On system. The requirements for user identification, access control, and integration with other systems and applications are often described in these specifications.
Industry associations and standards bodies have created a number of various SSO specifications, including:
- Security Assertion Markup Language (SAML): An established mechanism for communicating authentication and permission information across systems is Security Assertion Markup Language (SAML). By enabling a user to check in to one system and then access other systems without having to log in again, it is frequently used to create Single Sign-On.
- OpenID Connect: An open standard for user authentication using OAuth (an authorization protocol) is known as OpenID Connect. It is frequently used to give web-based applications SSO features.
- Kerberos: Using a single set of login credentials, users can access several systems and services using the network authentication technique known as Kerberos. Single Sign-On is frequently used using it in business settings.
- LDAP: LDAP is a protocol for managing and gaining access to directory services, which include those that house user authentication data. By enabling users to authenticate just once and access various systems without having to do so again, it can be used to build SSO.
Overall, SSO specifications outline the prerequisites and best practices for putting a Single Sign-On system into place and are crucial to guaranteeing the system’s effectiveness, efficiency, and security.
SSO certification
A Single Sign-On solution is tested to make sure it complies with specific standards or requirements as part of the Single Sign-On (SSO) certification process. This could entail evaluating the solution’s interoperability, performance, security, and other features.
SSO certification programs are offered by a number of organizations, including:
- The OpenID Foundation: Open standards for user-centric identity and SSO are encouraged by the OpenID Foundation, a business organization. It provides a certification scheme for the Single Sign-On specification known as OpenID Connect.
- OASIS: OASIS is a nonprofit group that creates and promotes standards for many different sectors, including identification and SSO. It provides an SSO specification certification program for SAML.
- The Kantara Initiative: The Kantara Initiative is a business group that concentrates on standards for identification and privacy, including SSO. SAML, OpenID Connect, and other Single Sign-On protocols, it offers a certification program.
Organizations can make sure that their Single Sign-On solution complies with requirements and is appropriate for usage in their environment by obtaining SSO certification. Users may also receive confidence from it that the solution is trustworthy and safe.
What is SAP SSO? | How SAP SSO works?
With the help of the authentication and authorization tool SAP Single Sign-On (SAP SSO), users can log into numerous SAP systems using just one set of login credentials. In order to authenticate users and grant them access to SAP systems and applications, it offers a safe, simple, and centralized method. With SAP SSO, users only need to provide their login information once and can access all SAP systems to which they have been granted access without receiving a second question. In addition to increasing user productivity, this lowers the chance of password-related security breaches. Do you have any particular concerns regarding SAP SSO?
Single Sign-On for the SAP GUI
Yes, single sign-on (SSO) capabilities can be provided for the SAP GUI using SAP Single Sign-On (SAP SSO). Users only need to input their login information once when Single Sign-On is enabled for the SAP GUI, and they may then access all SAP systems and applications that they are permitted to use without being prompted to do so.
Installing and configuring SAP Single Sign-On on your SAP systems is necessary, as is installing the SAP GUI on the client computers in order to allow SSO for the SAP GUI. Once SAP SSO is set up, users can access all permitted SAP systems and apps by logging in to the SAP GUI with their SAP Single Sign-On credentials without being asked for another set of credentials.
Please feel free to ask any particular questions you may have regarding setting up SAP SSO for the SAP GUI.
What are SAP SSO Prerequisites?
You should take into account the following requirements before deploying SAP Single Sign-On (SAP SSO):
Releases of SAP NetWeaver that are supported include versions 7.0 and higher.
- Client operating systems supported: Windows, macOS, and Linux are just a few of the client operating systems that SAP SSO is compatible with.
- Web browsers that are supported Web browsers including Internet Explorer, Google Chrome, Mozilla Firefox, and Safari all enable SAP Single Sign-On.
- SAP NetWeaver prerequisites: You must have the following SAP NetWeaver components installed in order to use SAP Single Sign-On:
- Cryptographic Library for SAP (SAPCRYPTOLIB)
- Security Services for SAP (SAPSECULIB)
- Required user management: To manage user accounts and permissions, you must have an SAP user management system in place, such as SAP Identity Management (SAP IDM) or SAP User Management Engine (SAP UME).
- Network infrastructure required: SAP SSO needs a network architecture that supports HTTPS-based secure communication.
You must have at least one SAP system that has been set up for SAP Single Sign-On.
FAQ:
1. Why SAML is used for SSO?
A frequently used standard for transmitting authentication and permission information across systems is Security Assertion Markup Language (SAML). By enabling a user to check in to one system (like a company’s internal network) and then access other systems (like cloud-based services) without having to log in again, it is frequently used to achieve Single Sign-On (SSO).
There are a number of reasons why businesses may decide to utilize SAML for SSO:
- Widely-supported: SAML is a well-known and popular protocol that is supported by a wide range of systems and applications. Because Single Sign-On solutions need to support a lot of systems, this makes it simple to interface with a variety of systems and applications.
- Secure: To guarantee the security of the authentication and authorization data that is sent between systems, SAML uses digital signatures and encryption. This makes user credentials secure and helps guard against unlawful access.
- User-friendly: SAML is user-friendly because it enables users to sign in once to one system and then access others without having to do so again. The user experience is seamless and practical as a result.
- Scalable: SAML is excellent for businesses with a large number of users and systems because it is built to enable large-scale deployments.
- Flexible: SAML is adaptable enough to satisfy the needs of many different businesses because it supports a wide range of authentication techniques, such as username and password, multifactor authentication, and others.
2. What is the difference between SSL and SAML?
Although both Protect Sockets Layer (SSL) and Security Assertion Markup Language (SAML) are technologies used to secure communication and the flow of data over the internet, they are utilized for various reasons and function in various ways.
An encrypted connection between a web server and a client is established using the SSL protocol (such as a web browser). In order to safeguard online transactions and communication, it is frequently used to encrypt the transmission of sensitive data, such as credit card information or login credentials.
Contrarily, SAML is a protocol for transferring authentication and authorization information across systems. It is frequently used to achieve Single Sign-On (SSO), which enables a user to check in to one system (like a business’s internal network) and then access other systems (like cloud-based services) without having to do so again. For secure resource access both within and between companies, SAML is frequently utilized.
The primary distinction between SSL and SAML is that whereas SAML is used to share identity and authorization information between systems, SSL is used to create an encrypted connection between a client and a server. Web connections are frequently secured using SSL, but Single Sign-On is frequently secured using SAML.
3. Why is SAML better than OAuth?
Both the OAuth (Open Authorization) and Security Assertion Markup Language (SAML) protocols are used to grant safe access to resources. They serve various functions and operate in various ways, though.
A protocol called SAML is used to transfer authentication and authorization information across systems. By enabling a user to check in to one system (like a company’s internal network) and then access other systems (like cloud-based services) without having to log in again, it is frequently used to achieve Single Sign-On (SSO). Secure access to resources within or between organizations is frequently provided using SAML.
OAuth, on the other hand, is a mechanism for authorizing access to protected resources for third-party apps. It is frequently employed to enable users to grant consent for one application (like a social networking platform) to access data (like their contacts’ photographs or photos) that is kept on another application (such as a photo-sharing website). OAuth is frequently employed to grant secure access to resources that belong to a person as opposed to an organization.
The following are some significant distinctions between SAML and OAuth:
- Goal: OAuth is mostly used for authorization, whereas SAML is primarily used for single sign-on.
- Scope: OAuth is often used to provide access to resources that are owned by a person, whereas SAML is typically used to provide access to resources that are owned by an organization or between organizations.
- Integration: OAuth is often used to allow access to third-party applications, whereas SAML is typically integrated into an organization’s current identity management infrastructure.
Overall, an organization’s specific requirements and the resources they are attempting to secure will determine whether SAML or OAuth is “better.” OAuth may be a better option for businesses that need to let users grant third-party applications access to their private resources, but SAML may be a better option for those that need to offer secure and convenient access to a vast number of systems and applications.
Who uses SAML authentication?
A frequently used standard for transmitting authentication and permission information across systems is Security Assertion Markup Language (SAML). By enabling a user to check in to one system (like a company’s internal network) and then access other systems (like cloud-based services) without having to log in again, it is frequently used to achieve Single Sign-On (SSO). Secure access to resources within or between organizations is frequently provided using SAML.
Many different organizations, including the following, employ SAML authentication:
- Enterprises: SAML is frequently used by businesses to offer secure access to a range of on-premises and cloud-based systems and apps.
- Government agencies: Providing safe access to resources like online services and systems, government entities frequently employ SAML.
- Educational institutions: To offer secure access to learning management systems, student portals, and other resources, educational institutions typically employ SAML.
- Healthcare organizations: To enable secure access to electronic health records and other sensitive resources, healthcare companies frequently employ SAML.
Overall, a large number of companies employ SAML authentication to offer convenient and safe access to resources.
What is Single Sign On (SSO) and how does it work?
A single set of login credentials can be used by users to log into multiple applications utilizing the Single Sign On (SSO) authentication method. A user can access several systems or apps without having to check in again at each one when they log in using SSO since a central authentication service authenticates them.
Why is Single Sign On (SSO) important?
By reducing the number of sites where login credentials must be stored and managed, SSO is crucial since it improves security. Lowering the number of distinct authentication systems that must be handled and linked, also makes IT management simpler. By lowering the number of login screens users must go through and making it simpler for users to access the resources they require, SSO enhances the user experience.
How can I access Single Sign On (SSO)?
The specific way to access SSO depends on how it is deployed in your company. To manage SSO, many businesses employ a centralized authentication provider like Okta or OneLogin. Users can access SSO in this situation by logging into the website or application of the central authentication provider. Users can access SSO via logging into one of the federated identity systems used by some businesses, such as SAML or OpenID Connect, which handle SSO.
What is the primary advantage of Single Sign On (SSO)?
The main benefit of SSO is that users may log into numerous systems or apps with just one set of login credentials. Users will find it more convenient as a result of not having to remember and enter different login credentials for each program they use. By minimizing the number of locations where login credentials must be stored and handled, SSO also increases security.
What are the advantages and disadvantages of Single Sign On (SSO)?
Convenience, greater security, improved user experience, and easier IT management are all benefits of SSO. One point of failure, data protection issues, and the requirement for additional infrastructure are possible drawbacks. SSO is a preferred authentication mechanism in many organizations since the benefits typically exceed the drawbacks.

