A web application firewall (WAF) is a security tool that is specifically designed to protect web applications from various types of attacks. A WAF works by examining incoming web traffic and blocking malicious requests that could compromise the security of a web application. WAFs can be implemented as hardware appliances, software programs, or cloud-based services. WAFs are typically used to protect web applications from attacks such as cross-site scripting (XSS), SQL injection, and other types of injection attacks.
Web application firewall, WAF provides protection for HTTP and HTTPS protocols for any web server, or for any world appliance which is offering web services. WAF is very sensitive in nature and works on mainly the application layer of the OSI model.
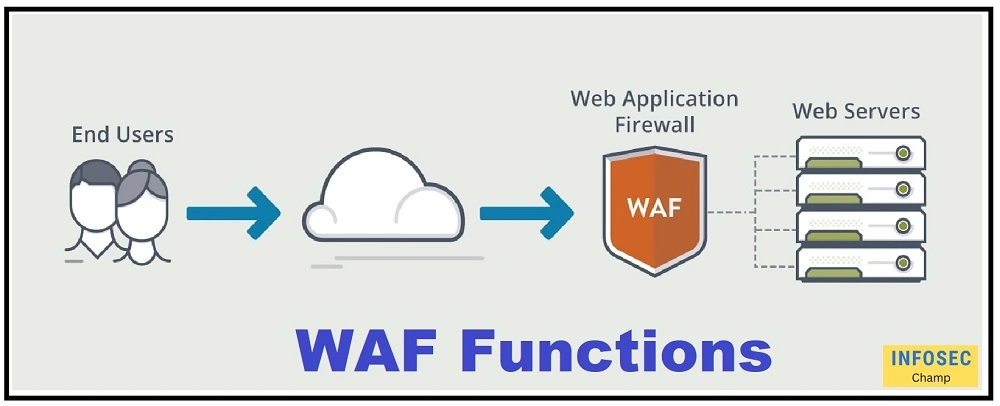
WAF gets configured with different rules for the protection of web servers and web services. the web server can be public internet facing or can be intranet based too.
WAF also provides protection against Open Web Application Security Project (OWASP) top 10 vulnerabilities, these top 10 vulnerabilities from the market should be taken care of for web protection against the web server and web services.
WAF can play a hardware appliance or a software-hardened operating system is an appliance.
WAF can be configured in monitoring mode for checking on what is going on in the web server. after sometime when one finds enough data points and decision points.
WAF provides two different types of protection methods which are
- Whitelisting of the traffic and ports
- Blocklist of the traffic and ports
What are WAF and WAF types?
There are WAF nowadays available for
- Network,
- Cloud, and
- Host-based devices.
Web Application Firewall project
Projects related to web application firewalls could be adopted by those candidates or trainees who want to make their career in web security, web development, and related security.
The project should include different types of vulnerable protection, this protection must include all the OWASP top 10 criteria.
The delivery of the project should be somewhere between 6 months to 9 months.
Web application firewall Azure | Azure WAF
Azure Web Application Firewall (WAF) is a cloud-based security service that provides protection for web applications by blocking malicious traffic and enabling users to create custom rules to control traffic to their web applications. It is designed to help businesses protect their web applications from a variety of threats, including cross-site scripting (XSS), SQL injection attacks, and malicious bot activity.
To use Azure WAF, you will need to sign up for an Azure account and configure the service to protect your web application. This typically involves adding your web application as a protected resource, setting up rules to control traffic, and configuring other security features as needed. Azure WAF can be used in conjunction with Azure Load Balancer and Azure Application Gateway to provide additional security and performance benefits.
Azure WAF offers a variety of features and benefits, including the ability to block or allow traffic based on custom rules, integration with Azure Monitor for logging and alerting, and support for multiple deployment options including public, private, and hybrid cloud environments.
Web application firewall AWS
Amazon Web Services (AWS) offers a web application firewall (WAF) service called AWS WAF that helps protect web applications from common web exploits that could affect application availability, compromise security, or consume excessive resources.
AWS WAF can be used to block malicious traffic by applying rules to incoming HTTP/S requests. These rules can be based on the characteristics of the request such as the IP address, the values of headers and query string parameters, and the patterns in the request body. AWS WAF also includes a library of pre-configured rules that cover common web exploits such as cross-site scripting (XSS) and SQL injection attacks.
To use AWS WAF, you will need to sign up for an AWS account and configure the service to protect your web application. This typically involves creating a web ACL (access control list) and adding rules to it to control traffic to your web application. AWS WAF can be used in conjunction with other AWS services such as Amazon CloudFront and Amazon API Gateway to provide additional security and performance benefits.
AWS WAF offers a variety of features and benefits, including the ability to block or allow traffic based on custom rules, integration with AWS CloudWatch for logging and alerting, and support for multiple deployment options including public, private, and hybrid cloud environments.
AWS, Amazon Web Services which is the biggest cloud service provider in the world offers different types of WAF protection, this WAF protection is also available on different layers of the cloud elements like different VPC, different gateway, and different levels of web services.
AWS shield with web ACL also acts and helps with WAF functionality. there are two different editions and those are AWS standard and AWS advance. AWS advance has several additional security features over the AWS standard edition. if you check cost wise standard is cost-effective compared to the advance one.
Best Web application firewall vendors, WAF OEMs, WAF support partners
- Cloudflare WAF
- AWS WAF
- AppTrana
- Prophaze WAF
- Akamai
- Sucuri Website Firewall
- Imperva
- F5 Advanced | F5 WAF
- Barracuda
- Fortinet Fortiweb
- SiteLock
- Citrix WAF
One should conduct a proof of concept (POC) for a few weeks to a few months, depending on the number of web servers and web services that need to be secured, to determine whether the WAF is appropriate for your environment and the protection of web services.
You will select the product, OEM, make, and model that best suits you after doing a proper POC.
Best top 10 benefits of WAF
A number of benefits are available to businesses that use web application firewalls (WAFs) to protect their websites and online applications. The following ten benefits of using a WAF are summarised:
- Protect against common web vulnerabilities: Cross-site scripting (XSS), SQL injection attacks, and remote file inclusion are examples of typical online vulnerabilities that WAFs can assist defend against.
- Prevent malicious traffic: By applying rules to incoming HTTP/S requests based on factors like IP address, request headers, and query string parameters, WAFs can block malicious traffic.
- Enhance compliance: By offering defense against threats like data breaches and unauthorised access, WAFs can assist firms in meeting compliance standards.
- Enhance security: By adding an extra layer of defence for web applications, WAFs can assist enterprises in improving their overall security posture.
- Enhance performance: By delegating security processes to the WAF and utilising capabilities like load balancing and caching, WAFs can aid in enhancing the efficiency and scalability of web applications.
- Simplify security management: By offering a centralised point of control for web application security, WAFs can assist in simplifying security management.
- Cost-saving: WAFs can assist cut expenses by doing away with the requirement for unique security solutions for every web application.
- Support for cloud and hybrid settings: WAFs can be implemented in cloud, on-premises, and hybrid environments, making them appropriate for a variety of enterprises.
- Offer adaptability: WAFs can be tailored to an organization’s unique security requirements, offering adaptability to meet evolving security requirements.
- Enhance user experience: By preventing fraudulent traffic and maintaining the availability and efficiency of web applications, WAFs can contribute to an improvement in user experience.
Web application firewall interview questions
In general, the interviewer is interested in questions about web application firewalls (WAFs), including their types, functions, and protocols that they support.
Any business that employs a security professional with experience in web application firewalls wants to have a staff member who can manage their web server and web services securely. Data security and cyber security should be understood.
Candidate should be knowledgeable about various OEMs, their goods, and the advantages of what they offer.
The WAF cybersecurity interview questions also address various operating system kinds, how operating systems work, and the features and benefits of specific brands make, and models.
Web application firewall versus network firewall | What is the difference between WAF and firewall?
Web application firewalls, or WAFs, are security function providers at the application layer while network firewalls are OSI layer 3 capability providers at the third layer.
The network firewall primarily provides security against network threats and assaults, which can be from the network from the Internet or within LAN. A typical WAF is regarded as a sophisticated and the front layer of any web series or web server.

What is prophaze WAF?
A web application firewall (WAF) called Prophaze is made to defend websites and web applications against online threats. It employs a range of strategies, such as signature-based detection, behavioral analysis, and machine learning, to find and stop harmful traffic.
Prophaze WAF may be set up on-premises or in the cloud and works with a variety of operating systems, including Linux, Windows, and MacOS. It offers defense against numerous risks, such as malicious bot activity, SQL injection assaults, and cross-site scripting (XSS).
Prophaze WAF includes features like load balancing, content delivery, and caching in addition to its security capabilities to aid in enhancing the performance and scalability of web applications.
Any prerequisite for prophaze?
A security tool that may be used to defend websites and web applications from online threats is called Prophaze WAF. There are typically no requirements beyond having a website or web application to defend and access to the Prophaze WAF service because it is meant to be simple to deploy and configure.
Prophaze WAF deployment may have some particular requirements or considerations, depending on your choice. For instance, you will need to have a proper server environment and infrastructure in place if you are running Prophaze WAF on-premises. You must create an account and configure the Prophaze WAF service to defend your website or web application if you use the cloud-based version of the service.
It is typically advised to have some acquaintance with web security ideas and procedures, as well as prior management expertise with web servers and apps, in either situation. This can assist you in getting the most out of the Prophaze WAF solution and guarantee that it is set up correctly to safeguard your digital assets.
How to implement prophaze?
There are several ways to implement Prophaze WAF, depending on your specific needs and requirements. Here are some general steps you can follow to get started with Prophaze WAF:
- Sign up for a Prophaze WAF account: If you are using the cloud-based version of Prophaze WAF, you will need to sign up for an account and select a pricing plan that meets your needs.
- Configure the Prophaze WAF service: Once you have an account, you will need to configure the Prophaze WAF service to protect your website or web application. This typically involves adding your website or web application as a protected resource, setting up rules to control traffic, and configuring other security features as needed.
- Deploy the Prophaze WAF service: Next, you will need to deploy the Prophaze WAF service in front of your website or web application. This can be done either on-premises or in the cloud, depending on your preferences and requirements.
- Test and verify the Prophaze WAF service: Once the Prophaze WAF service is deployed, it is important to test and verify that it is working properly. This can be done using a variety of tools and techniques, such as manually testing the service, using automated testing tools, or simulating cyber attacks.
- Monitor and maintain the Prophaze WAF service: After the Prophaze WAF service is deployed, it is important to monitor its performance and effectiveness, and make any necessary updates or changes to ensure that it continues to provide the desired level of protection.
It is generally recommended to work with a security expert or IT professional when implementing Prophaze WAF, to ensure that it is properly configured and deployed to protect your web assets.
API Security Prophaze
Prophaze APIs can be secured using WAF, a web application firewall (WAF), from cyberattacks and other security risks. It employs a range of strategies, such as signature-based detection, behavioral analysis, and machine learning, to find and stop harmful traffic.
You must register for a Prophaze WAF account and set the service up to secure your APIs in order to utilize it to defend them. Typically, this entails adding your APIs as protected resources, creating traffic rules, and installing additional security features as necessary. Prophaze WAF may be set up on-premises or in the cloud and works with a variety of operating systems, including Linux, Windows, and MacOS.
Prophaze WAF includes features like load balancing, content delivery, and caching in addition to its security capabilities to help with the performance and scalability of your APIs. When using Prophaze WAF, it is typically advised to engage with a security expert or IT specialist to make sure that it is set up and deployed to protect your APIs correctly.
FAQ:


