Cloud Access Security Broker, or CASB, is an acronym. It is a security tool created to safeguard an organization’s users and data while they access cloud-based programs and services. To make sure that only authorized access and actions are allowed, CASBs enforce security regulations while intercepting and inspecting traffic between the user and the cloud service. They offer several security features, including as authentication, access control, data loss prevention (DLP), threat protection, and compliance management. They can also be used to secure access to Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) products. They are frequently used to secure access to Software as a Service (SaaS) applications, such as Office 365, Salesforce, and Google Workspace.
CASBs can be set up in a number of different ways, such as cloud services, on-premises appliances, or hybrid solutions. They can assist enterprises in protecting their data and users when utilizing cloud-based services and are a crucial part of an all-encompassing cloud security plan.
What is a CASB used for? | CASB full form in cyber security
Platform as a Service (PaaS), Infrastructure as a Service (IaaS), and Software as a Service (SaaS) offers are examples of cloud-based applications and services that employ CASBs to safeguard access. They offer a variety of security features to assist in achieving this goal and are meant to safeguard an organization’s data and users when accessing these resources.
Following are some particular use cases for CASBs:
- Authentication: These can help to enforce strong authentication policies, such as multi-factor authentication, to ensure that only authorized users are able to access the cloud services.
- Access control: These can help to enforce fine-grained access controls to ensure that users only have access to the resources they need to do their job.
- Data loss prevention (DLP): These can help to prevent data leakage (for data security) by detecting and blocking sensitive data from being exfiltrated from the cloud.
- Threat protection: These can help to protect against threats such as malware and phishing attacks by intercepting and inspecting traffic between the user and the cloud service.
- Compliance management: These can help organizations to ensure compliance with various regulations and standards, such as HIPAA and GDPR, by enforcing policies and providing reports and audits.
In conclusion, CASBs are employed to safeguard access to cloud-based resources and defend against a range of dangers, as well as to assist firms in adhering to regulatory standards.
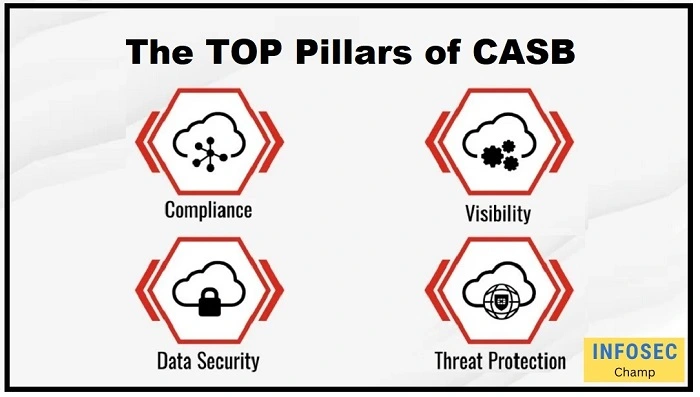
What are the 4 pillars of CASB?
CASB (Cloud Access Security Broker) is commonly thought of as having four pillars, which are as follows:
- Visibility: These give people inside of an organization visibility into the cloud-based resources they are accessing, as well as the kinds of resources they are accessing and the activities they are taking. This enables firms to comprehend the dangers involved with these operations and implement the necessary precautions to reduce them.
- Compliance: By enforcing policies, generating reports, and conducting audits, can assist firms in ensuring compliance with a variety of laws and standards, including HIPAA and GDPR.
- Data protection: By identifying and preventing the exfiltration of sensitive data from the cloud, they can aid in preventing data leaks.
- Threat protection: By intercepting and examining traffic between the user and the cloud service, can assist in defending against dangers like malware and phishing assaults.
These four pillars are linked and function as a unit to support enterprises in protecting their users and data when utilizing cloud-based services.
What is the difference between CASB and DLP?
Data loss prevention (DLP) and cloud access security broker (CASB) are two security solutions made to safeguard an organization’s data, although they work differently.
Access to cloud-based apps and services is secured via CASB, a security solution. To guarantee that only authorized access and actions are allowed, it intercepts and inspects traffic between the user and the cloud service while enforcing security policies. These offer a variety of security features, such as threat protection, authentication, access control, and compliance management.
DLP is a security tool that stops sensitive data from leaving a business by spotting and stopping attempts to do so. To assess whether data is sensitive or not, it often scans data in real time and compares it to a set of predetermined rules or policies. DLP can take a number of steps to stop sensitive data from being leaked if it is found, including banning the action, encrypting the data, or warning the user or administrator.
While both CASB and DLP are used to protect data, their operation and focus regions differ at various points in the data lifecycle. While DLP focuses on avoiding data leakage, CASB secures access to cloud-based resources. As a result, they can be combined as a component of an all-encompassing security plan.
Does CASB replace VPN?
Although both CASB (Cloud Access Security Broker) and VPN (Virtual Private Network) are security solutions used to secure access to resources, their methods of operation and intended uses differ.
A virtual private network, or VPN, is a networking technology that establishes a safe, encrypted connection between a client and a server over a shared or public network like the internet. To enable remote users to safely access resources on a private network, like a corporate network, VPNs are frequently employed.
Contrarily, CASB is a security tool that is employed to protect access to cloud-based programs and services. To guarantee that only authorized access and actions are allowed, it intercepts and inspects traffic between the user and the cloud service while enforcing security policies. They offer several security features, including authentication, access control, data loss prevention (DLP), threat protection, and compliance management.
While CASB and VPN can both be used to safeguard access to resources, their functions and points of operation are distinct. While these are focused on safeguarding access to cloud-based services and defending against a variety of threats, VPNs are primarily concerned with establishing a secure connection between a client and a server. As a result, as part of a comprehensive security plan, CASB often works in addition to VPN rather than as a replacement.
CASB vendors
Solution providers for Cloud Access Security Broker (CASB) include the following:
- McAfee
- Symantec
- Cisco
- Forcepoint
- Zscaler
- Bitglass
- Skyhigh Networks (now part of McAfee)
- Elastica (now part of Blue Coat)
- Proofpoint
- Imperva
These suppliers provide a range of CASB solutions that can be set up in a number of different ways, such as cloud services, on-premises appliances, or hybrid solutions. They offer a variety of security features, including threat protection, authentication, access control, and data loss prevention (DLP).
It’s crucial to take into account aspects like the required security capabilities, the preferred deployment architecture, and the interface with any existing security solutions when selecting a CASB vendor. The reputation and performance of the provider in the market should also be taken into account.
CASB architecture
In order to safeguard access to cloud-based resources, a Cloud Access Security Broker (CASB) solution’s architecture typically comprises of a number of interconnected components.
The parts that are commonly present in a CASB architecture are summarised as follows:
- User client: The hardware or software that a user is utilizing to access cloud-based resources It might be a laptop, desktop, smartphone, or web browser.
- Cloud service: The user is attempting to access a cloud service, which is an online program or service. It might be a platform as a service (PaaS), infrastructure as a service (IaaS), or software as a service (SaaS) program like Salesforce or Office 365.
- CASB proxy: This solution’s CASB proxy is the part that examines and intercepts communication between the user client and the cloud service. Based on the findings of the inspection, it enforces security regulations and takes action.
- Security policy engine: Based on the user’s identity, role, and the type of access or activity being conducted, the security policy engine of the CASB solution is in charge of implementing security policies. It chooses whether to approve or reject the request.
- Management console: Administrators set up and manage the CASB solution via the management console, which is a component of this solution. It often offers a variety of functions, including reporting, analytics, and policy management.
Integration with other security solutions: To offer a more thorough security posture, CASB solutions frequently integrate with other security solutions like firewalls, intrusion prevention systems (IPS), and data loss prevention (DLP) solutions.
This is a general description of the parts that are frequently present in CASB architectures. Depending on the vendor and the particular requirements of the company, the precise elements and capabilities of a CASB solution may change.
Microsoft CASB
Azure Information Protection is a Cloud Access Security Broker (CASB) service provided by Microsoft. When accessing cloud-based resources like Microsoft’s own Office 365 and Azure platforms, Azure Information Protection is made to assist enterprises in safeguarding their data.
A variety of security features are offered by Azure Information Protection, including:
- Data classification: Users may choose to manually classify data or have Azure Information Protection automatically classify data based on established rules or policies.
- Data labeling: To help identify and secure sensitive information, users of Azure Information Protection can tag data with metadata.
- Data protection: Depending on the classification and label of the data, Azure Information Protection can apply encryption and other security rules to secure it.
- Access control: Fine-grained access controls can be enforced by Azure Information Protection to make sure that users only have access to the resources they require to perform their duties.
Compliance management: By enforcing policies, producing reports, and conducting audits, Azure Information Protection can assist enterprises in ensuring compliance with a variety of laws and standards, including HIPAA and GDPR.
When organizations access cloud-based services on the Microsoft platform, Azure Information Protection helps to secure their data and is a key part of Microsoft’s broader security strategy.
Azure CASB
Microsoft’s cloud computing platform Azure provides a variety of security options to assist businesses in protecting their data and resources when utilizing the platform. Azure Information Protection is one of these solutions. It is a Cloud Access Security Broker (CASB) solution made to assist businesses in safeguarding their data when utilizing cloud-based resources like Office 365 and Azure.
A variety of security features are offered by Azure Information Protection, including:
- Data classification: Users may choose to manually classify data or have Azure Information Protection automatically classify data based on established rules or policies.
- Data labeling: To help identify and secure sensitive information, users of Azure Information Protection can tag data with metadata.
- Data protection: Depending on the classification and label of the data, Azure Information Protection can apply encryption and other security rules to secure it.
- Access control: Fine-grained access controls can be enforced by Azure Information Protection to make sure that users only have access to the resources they require to perform their duties.
- Compliance management: By enforcing policies, producing reports, and conducting audits, Azure Information Protection can assist enterprises in ensuring compliance with a variety of laws and standards, including HIPAA and GDPR.
When organizations access cloud-based resources on the Azure platform, Azure Information Protection helps to secure their data and is a key part of Microsoft’s broader security strategy for Azure.
CASB solutions
When accessing cloud-based apps and services, an organization’s data and users are protected by Cloud Access Security Broker (CASB) solutions, which are security solutions. To ensure that only authorized access and actions are allowed, CASB solutions enforce security policies while intercepting and inspecting traffic between the user and the cloud service.
A number of security capabilities are offered by CASB solutions, such as:
- Authentication: To make sure that only authorized users can access the cloud services, this solution can help enforce strict authentication requirements, such as multi-factor authentication.
- Access control: By enforcing fine-grained access controls, this solution can help to make sure that users only have access to the resources they require to do their duties.
- Data loss prevention (DLP): This method can assist in preventing data leakage by identifying and preventing the exfiltration of sensitive data from the cloud.
- Threat protection: By intercepting and examining traffic between the user and the cloud service, this solution can help to defend against risks like malware and phishing assaults.
- Compliance management: By enforcing policies, generating reports, and conducting audits, this solution can assist firms in ensuring compliance with a variety of laws and standards, including HIPAA and GDPR.
Deploying CASB solutions as a cloud service, an on-premises appliance, or a hybrid solution is just a few of the options available. They can assist enterprises in protecting their data and users when utilizing cloud-based services and are a crucial part of an all-encompassing cloud security plan.
AWS CASB
When using the Amazon Web Services (AWS) cloud computing platform, businesses can use a variety of security options to protect their data and resources. One of these options is AWS Security Hub, a centralized platform for security management that works with other AWS security tools and outside options to give a comprehensive picture of a company’s security posture.
The following AWS Security Hub functionalities are pertinent to Cloud Access Security Broker (CASB) solutions:
- Compliance management: By offering compliance checks and automatic compliance reporting, AWS Security Hub may assist enterprises in ensuring compliance with a variety of laws and standards, including HIPAA and GDPR.
- Threat protection: To provide threat detection and response capabilities, AWS Security Hub connects with other AWS security technologies, such as Amazon GuardDuty.
- Access control: By integrating with existing AWS security solutions like AWS Identity and Access Management (IAM), AWS Security Hub may offer fine-grained access restrictions that guarantee users only have access to the resources they require to perform their jobs.
- Data protection: AWS Security Hub works in conjunction with other AWS security technologies, like AWS Key Management Service (KMS), to offer encryption and key management for data protection.
AWS Security Hub offers a variety of security capabilities that are pertinent to CASB and can be utilized as a part of an all-encompassing cloud security strategy, even though it does not offer all the features of a traditional CASB solution.
CASB vs SASE
Security solutions like CASB (Cloud Access Security Broker) and SASE (Secure Access Service Edge) are both created to safeguard an organization’s data and users when they access resources, but they function differently and have different goals.
Access to cloud-based apps and services is secured via CASB, a security solution. To ensure that only authorized access and actions are allowed, it operates by intercepting and inspecting traffic between the user and the cloud service and implementing security regulations. Authentication, access control, data loss prevention (DLP), threat protection, and compliance management are just a few of the security features offered by CASBs.
A secure connection between users and resources, independent of location, is made possible by SASE, a security solution. A single, cloud-delivered solution, it incorporates a number of security features, including VPN, firewall, and DLP. SASE solutions are frequently implemented as cloud services and are made to secure resource access from any location, using any device.
Although CASB and SASE are both used to secure access to resources, their functions and phases of operation are distinct. While SASE focuses on establishing a secure connection between users and resources, regardless of location, CASB is primarily concerned with protecting access to cloud-based resources. As a result, CASB and SASE can be applied in tandem as a component of an all-encompassing security approach.
CASB cyber security | CASB cyber security meaning | What does CASB mean in cyber security?
When accessing cloud-based apps and services, an organization’s users and data are protected by the Cloud Access Security Broker (CASB), a security solution. To make sure that only authorised access and actions are allowed, CASBs enforce security regulations while intercepting and inspecting traffic between the user and the cloud service.
CASBs offer a variety of security features, such as:
- Authentication: To make sure that only authorized users can access the cloud services, CASBs can assist in enforcing strict authentication requirements, such as multi-factor authentication.
- Access control: CASBs can assist in enforcing fine-grained access management to make sure that users only have access to the resources they require to do their duties.
- Data loss prevention (DLP): CASBs can aid in the prevention of data leakage by identifying and preventing the espionage of sensitive data from the cloud.
- Threat protection: By intercepting and examining traffic between the user and the cloud service, CASBs can assist in defending against threats like malware and phishing attempts.
- Compliance management: By enforcing policies, producing reports, and conducting audits, CASBs can assist enterprises in ensuring compliance with a variety of laws and standards, including HIPAA and GDPR.
CASBs are a crucial part of a thorough cybersecurity plan and can assist enterprises in protecting their users’ data and access to cloud-based services.
What is a CASB security | CASB security definition
When accessing cloud-based apps and services, an organization’s users and data are protected by the Cloud Access Security Broker (CASB), a security solution. To make sure that only authorised access and actions are allowed, CASBs enforce security regulations while intercepting and inspecting traffic between the user and the cloud service.
CASBs offer a variety of security features, such as:
- Authentication: To make sure that only authorized users can access the cloud services, this can assist enforce strict authentication requirements, such as multi-factor authentication.
- Access control: These can assist in enforcing fine-grained access controls to make sure users only have access to the resources they require to do their duties.
- Data loss prevention (DLP): These can assist in stopping data leakage by identifying and preventing the exfiltration of sensitive data from the cloud.
- Threat protection: By intercepting and examining traffic between the user and the cloud service, can assist in defending against dangers like malware and phishing assaults.
- Compliance management: By enforcing policies, producing reports, and conducting audits, compliance management can assist firms in ensuring compliance with a variety of laws and standards, including HIPAA and GDPR.
These are crucial elements of a thorough security strategy that can assist firms in protecting their users and data when utilizing cloud-based services.
FAQ:
What is CASB in cyber security?
When accessing cloud-based apps and services, an organization’s users and data are protected by the Cloud Access Security Broker (CASB), a security solution. These operate by enforcing security policies to guarantee that only authorized access and actions are allowed, intercepting and inspecting traffic between the user and the cloud service.
What does a CASB do?
When accessing cloud-based apps and services, an organization’s users and data are protected by a security solution called a cloud access security broker. These operate by enforcing security policies to guarantee that only authorized access and actions are allowed, intercepting and inspecting traffic between the user and the cloud service.
CASBs offer a variety of security features, such as:
- Authentication
- Access control
- Data loss prevention (DLP)
- Threat protection
- Compliance management
What is the difference between CASB and SIEM?
Security solutions like CASB (Cloud Access Security Broker) and SIEM (Security Information and Event Management) are made to safeguard an organization’s data and resources, but they function differently and have different goals.
Access to cloud-based apps and services is secured via CASB, a security solution. To guarantee that only authorized access and actions are allowed, it intercepts and inspects traffic between the user and the cloud service while enforcing security policies. They offer several security features, including authentication, access control, data loss prevention (DLP), threat protection, and compliance management.
Comparatively, SIEM is a security solution that is used to gather, examine, and report security-related data and events from many sources, including network devices, servers, and apps. Security analysts can monitor security activities on a centralized platform using SIEMs to look for potential risks. They also give enterprises access to a variety of reporting and analytic tools to aid in understanding and handling security problems.
The data and resources of an organization are secured and protected by both of these, but they have different functions and work at various phases of the security process. While SIEM is largely concerned with gathering, evaluating, and reporting security-related data and events, CASB is primarily concerned with securing access to cloud-based resources. As a result, CASB and SIEM can be utilized in tandem as a component of an all-encompassing security approach.
Is Microsoft Defender a CASB?
No, A Cloud Access Security Broker is not Microsoft Defender (CASB).
On computers running Microsoft Windows, Microsoft Defender is a security program that offers defense against malware and other dangers. A variety of security features are included, including real-time defense, threat detection and response, and device health monitoring.
Contrarily, CASB is a security tool that is employed to protect access to cloud-based programs and services. To guarantee that only authorized access and actions are allowed, it intercepts and inspects traffic between the user and the cloud service while enforcing security policies. They offer several security features, including authentication, access control, data loss prevention (DLP), threat protection, and compliance management.
In spite of the fact that both Microsoft Defender and CASB are used to safeguard and protect an organization’s data and resources, they have different functions and functions at various phases of the security process. This is focused on safeguarding access to cloud-based resources, whereas Microsoft Defender is largely focused on protecting against threats on devices running Microsoft Windows. As a result, Microsoft Defender and CASB can be combined as a component of an all-encompassing security approach.
Is CASB a firewall?
A firewall is not a Cloud Access Security Broker.
A firewall is a type of network security system that keeps track of and manages incoming and outgoing network traffic in accordance with pre-established security rules. It is often installed at the perimeter of a network to safeguard against external threats and is aimed to shield an organization’s resources from unwanted access and attacks.
Contrarily, CASB is a security tool that is employed to protect access to cloud-based programs and services. To guarantee that only authorized access and actions are allowed, it intercepts and inspects traffic between the user and the cloud service while enforcing security policies. They offer several security features, including authentication, access control, data loss prevention (DLP), threat protection, and compliance management.
Although both firewalls and CASBs are employed to secure and safeguard the information and assets of an organization, they have different functions and functions at various phases of the security process. While these are focused on safeguarding access to cloud-based resources, firewalls are primarily focused on protecting against external threats at the network perimeter. As a result, firewalls and CASBs can be combined as a component of an all-encompassing security strategy.