The network resources of an organization are maintained and stored by Active Directory, which is a directory service (important information for active directory security). It serves as a central repository for the user, computer, and network resources and controls access to them as well as their security. The Lightweight Directory Access Protocol (LDAP) is a protocol for using an IP network to access and maintain distributed directory information services. Active-Directory directory data is accessed and managed using LDAP.
A broad variety of directory-enabled applications use LDAP to handle the organization, maintenance, and exchange of directory information, such as user and group information. In order to handle user and group information and to offer authentication and authorization services, Active Directory is frequently used in conjunction with LDAP, which offers a common interface for accessing and maintaining directory information.
Active directory security best practices
Here are some best practices for securing Active Directory:
- Implement strong password policies: Ensure that users are required to use strong passwords and that passwords are regularly rotated.
- Enable two-factor authentication: Use two-factor authentication to provide an additional layer of security for accessing Active-Directory resources.
- Use Group Policy Objects (GPOs) to control access: Use GPOs to control access to Active-Directory resources and to enforce security policies.
- Monitor access to Active Directory: Use tools to monitor access to Active Directory resources and to detect and alert on any suspicious activity.
- Implement least privilege: Grant users the minimum level of access they need to perform their job duties and no more.
- Use security groups: Use security groups to control access to Active Directory resources, rather than assigning permissions directly to users.
- Use secure communication protocols: Use secure communication protocols such as LDAPS or Kerberos to protect the transmission of sensitive data between Active-Directory servers and clients.
- Regularly update and patch your systems: Keep your systems up to date with the latest security patches to help protect against vulnerabilities.
- Back up your data: Regularly back up your Active-Directory data to ensure that it can be recovered in the event of a disaster.
- Educate your users: Educate your users about best practices for securing their accounts and the importance of following security policies.
Active directory security checklist
Here is a checklist of security measures that can be implemented to secure Active Directory:
- Implement strong password policies: Ensure that users are required to use strong passwords and that passwords are regularly rotated.
- Enable two-factor authentication: Use two-factor authentication to provide an additional layer of security for accessing Active Directory resources.
- Use Group Policy Objects (GPOs) to control access: Use GPOs to control access to Active-Directory resources and enforce security policies.
- Monitor access to Active Directory: Use tools to monitor access to Active-Directory resources and to detect and alert on any suspicious activity.
- Implement least privilege: Grant users the minimum level of access they need to perform their job duties and no more.
- Use security groups: Use security groups to control access to Active-Directory resources, rather than assigning permissions directly to users.
- Use secure communication protocols: Use secure communication protocols such as LDAPS or Kerberos to protect the transmission of sensitive data between Active Directory servers and clients.
- Regularly update and patch your systems: Keep your systems up to date with the latest security patches to help protect against vulnerabilities.
- Back up your data: Regularly back up your Active-Directory data to ensure that it can be recovered in the event of a disaster.
- Educate your users: Educate your users about best practices for securing their accounts and the importance of following security policies.
Active directory security tools
There are several tools available for securing Active-Directory:
- Group Policy Objects (GPOs): GPOs are used to control access to Active-Directory resources and to enforce security policies.
- Active Directory Domain Services (AD DS): AD DS is a directory service that stores and manages the network resources of an organization.
- Active Directory Federation Services (AD FS): AD FS is a software component that provides single sign-on (SSO) capabilities for users to access multiple applications with a single set of credentials.
- Active Directory Rights Management Services (AD RMS): AD RMS is a security feature that enables the creation and enforcement of information rights for documents and emails.
- Microsoft Identity Manager (MIM): MIM is a tool that helps organizations manage user identities and access to resources.
- Azure Active Directory (Azure AD): Azure AD is a cloud-based directory service that provides identity and access management capabilities for cloud-based applications.
- Microsoft Security Compliance Manager (SCM): SCM is a tool that helps organizations plan, assess, and deploy security baselines for their systems.
- Microsoft Advanced Threat Analytics (ATA): ATA is a tool that uses machine learning and behavioral analytics to detect and alert on suspicious activity within an organization’s network.
- Network Access Protection (NAP): NAP is a security feature that helps ensure that only compliant computers are granted access to the network.
Microsoft BitLocker: BitLocker is a data encryption tool that helps protect data on a computer’s hard drive.
Active directory security assessment
The security of an organization’s Active Directory environment is evaluated through an Active Directory security assessment. This may entail locating potential weaknesses, assessing the efficacy of security measures, and giving suggestions for enhancing security.
An Active Directory security assessment should contain the following important steps:
- Identify the scope of the assessment: Determine what aspects of the Active-Directory environment will be included in the assessment.
- Gather information about the Active Directory environment: Collect data about the Active-Directory environment, including domain structure, user accounts, security policies, and other relevant information.
- Identify potential vulnerabilities: Look for potential vulnerabilities in the -Active-Directory environment, including weak passwords, unsecured communication protocols, and lack of access controls.
- Evaluate the effectiveness of security controls: Assess the effectiveness of the security controls in place, including password policies, access controls, and other measures.
- Make recommendations for improving security: Based on the findings of the assessment, make recommendations for improving the security of the Active Directory environment.
- Implement the recommendations: Put the recommendations into action to improve the security of the Active-Directory environment.
- Monitor and review: Monitor the Active-Directory environment on an ongoing basis and review the security assessment periodically to ensure that the security of the environment remains strong.
Active directory security groups
To control access to resources in Active Directory, security groups are utilised. To control access to resources, security groups are groups of user accounts, computer accounts, and other security concepts.
Use security groups for:
- Access to resources can be granted or denied using security groups. This includes network shares, files, and folders.
- Control resource access based on security group membership: Access to resources can be managed based on security group membership. For instance, access to a network share may be provided to members of a specific security group but restricted to non-members.
- Simplify the management of resource access: Security groups can be used to centrally manage resource access, making it simpler to restrict access to resources.
- Security groups may be local or international. Access to resources within a domain is controlled by local security groups, which are unique to that domain. Access to resources across domains is managed by global security groups.
- The Active-Directory Users and Computers console, as well as a variety of scripts and command-line tools, can be used to create and administer security groups.
Active directory security certification
There are several certifications available for professionals working with Active Directory and related technologies, including:
- Microsoft Certified: Azure Developer Associate: This certification demonstrates expertise in developing and maintaining applications using Azure services and Azure AD.
- Microsoft Certified: Azure Administrator Associate: This certification demonstrates expertise in managing Azure subscriptions, identities, storage, computing, and network resources.
- Microsoft Certified: Identity with Windows Server 2022: This certification demonstrates expertise in implementing, managing, and maintaining the identity and access solutions with Windows Server 2022.
- Microsoft Certified: Azure Security Engineer Associate: This certification demonstrates expertise in implementing, managing, and maintaining security in Azure.
- Microsoft Certified: Windows Server 2022 MCSA: This certification demonstrates expertise in installing, configuring, and maintaining Windows Server 2022.
- Microsoft Certified: Windows Server 2022 MCSE: This certification demonstrates expertise in designing, implementing, and maintaining the infrastructure for business-critical workloads.
- CompTIA Security+: This certification is vendor-neutral and covers a range of topics related to security, including network security, risk management, and identity and access management.
Many other Microsoft cloud-based certifications are also available.
There are many other certifications available for professionals working with Active Directory and related technologies. These certifications can help professionals demonstrate their knowledge and skills in these areas and can be useful for career advancement and professional development. Check more on IT professional available options.
Active directory security book
Here are a few books that cover Active Directory security:
- “Active Directory Security: Design, Deployment, and Maintenance” by Markk Soper, Scott Lowe, and Justin Menga: This book covers the design, deployment, and maintenance of Active-Directory security and includes practical guidance for securing Active Directory in complex environments.
- “Windows Server 2022 Inside Out: Services, Security, & Infrastructure” by Orin Thomas and Peter Ward: This book covers the services, security, and infrastructure of Windows Server 2022, including Active-Directory security.
- “Mastering Active Directory for Windows Server 2022” by Jordan Krause: This book covers the design, implementation, and management of Active Directory for Windows Server 2022, including security best practices.
- “Identity and Access Management (IAM) in Active Directory” by Markus Friedl: This book covers the design and implementation of Identity and Access Management (IAM) in Active Directory, including security best practices.
- “Active Directory: Designing, Deploying, and Running Active Directory” by Brian Desmond, Joe Richards, Robbie Allen, and Alistair G. Lowe-Norris: This book covers the design, deployment, and management of Active-Directory, including security best practices.

Top 10 Tips for Active directory security best practices
Here are some best practices for securing Active Directory:
- Implement strong password policies: Ensure that users are required to use strong passwords and that passwords are regularly rotated.
- Enable two-factor authentication: Use two-factor authentication to provide an additional layer of security for accessing Active-Directory resources.
- Use Group Policy Objects (GPOs) to control access: Use GPOs to control access to Active-Directory resources and to enforce security policies.
- Monitor access to Active Directory: Use tools to monitor access to Active Directory resources and to detect and alert on any suspicious activity.
- Implement least privilege: Grant users the minimum level of access they need to perform their job duties and no more.
- Use security groups: Use security groups to control access to Active-Directory resources, rather than assigning permissions directly to users.
- Use secure communication protocols: Use secure communication protocols such as LDAPS or Kerberos to protect the transmission of sensitive data between Active Directory servers and clients.
- Regularly update and patch your systems: Keep your systems up to date with the latest security patches to help protect against vulnerabilities.
- Back up your data: Regularly back up your Active-Directory data to ensure that it can be recovered in the event of a disaster.
- Educate your users: Educate your users about best practices for securing their accounts and the importance of following security policies.
Azure active directory security defaults
Azure Active Directory (Azure AD) Security Defaults is a security feature that provides a set of baseline security controls for Azure AD tenant. Security Defaults can be enabled for an Azure AD tenant to help protect against common threats and vulnerabilities, such as password spraying and pass-the-hash attacks.
Security Defaults provides the following security controls:
- Requiring multi-factor authentication (MFA) for administrators: Administrators are required to use MFA when signing in to Azure AD, to help protect against unauthorized access.
- Blocking legacy authentication protocols: Security Defaults blocks the use of legacy authentication protocols, such as NTLM and Kerberos, which are more vulnerable to attacks.
- Enforcing password complexity and expiration policies: Security Defaults enforces password complexity and expiration policies to help protect against password-based attacks.
- Requiring MFA for selected users: Security Defaults allows administrators to require MFA for selected users, such as users with privileged access or users who access sensitive resources.
- Monitoring for suspicious activity: Security Defaults monitors for suspicious activity, such as failed sign-in attempts or unusual sign-in locations, and sends alerts to administrators.
- Security Defaults can be enabled or disabled by an Azure AD tenant administrator. It is recommended to enable Security Defaults to help protect against common threats and vulnerabilities.
Dynamic active directory security groups
In Active Directory, dynamic security groups are those that have their membership determined by the contents of user characteristics. Administrators can construct groups that automatically include individuals that match specific criteria, such as department or job title, using dynamic security groups.
The requirements for participation in the group, such as the department attribute for users in the “Marketing” department, are specified by the administrator when creating a dynamic security group. A user is automatically assigned to the dynamic security group when they are created or changed in Active Directory and their department property is set to “Marketing.”
For controlling resource access and streamlining the process of providing or revoking access to users, dynamic security groups can be helpful. For instance, a network administrator can provide access to a network share and create a dynamic security group for users in the “Finance” department. Users’ membership in the dynamic security group will be immediately updated as they are added to or removed from the “Finance” department, making sure that access to the network share is always current.
The Active Directory Users and Computers console, as well as numerous command-line tools and scripts, can be used to create and administer dynamic security groups.
Mail enable active directory security group
To mail-enable a security group in Active Directory, you can use the Exchange Admin Center or the Exchange Management Shell.
To mail-enable a security group using the Exchange Admin Center:
- Open the Exchange Admin Center.
- In the left navigation, expand the Recipients tab and select Groups.
- Select the security group you want to mail-enable and click the Edit button.
- In the Edit Group window, click the Mail Settings tab.
- Check the “Mail-enable this group” box.
- Enter an email address for the group in the Email Address field.
- Click Save to apply the changes.
- To mail-enable a security group using the Exchange Management Shell:
- Open the Exchange Management Shell.
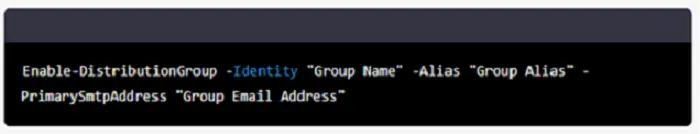
Type the following command and press Enter:
You can copy the script from below too.
Enable-DistributionGroup -Identity “Group Name” -Alias “Group Alias” -PrimarySmtpAddress “Group Email Address”
Replace “Group Name” with the name of the security group, “Group Alias” with the desired alias for the group, and “Group Email Address” with the email address you want to use for the group.
After mail-enabling the security group, you can use the group’s email address to send emails to all members of the group. Members of the group will also be able to use the group’s email address to send emails to the group.
FAQ:
1. How do I keep Active Directory secure?
Here are some best practices for securing Active Directory:
- Implement strong password policies
- Enable two-factor authentication
- Use Group Policy Objects (GPOs) to control access
- Monitor access to Active Directory
- Implement the least privilege
- Use security groups
- Use secure communication protocols
- Regularly update and patch your systems
- Back up your data
- Educate your users
2. What are the security features of Active Directory?
Active Directory includes several security features that can be used to help secure the network environment:
- Password policies: Active Directory allows administrators to set password policies, such as password complexity, length, and expiration, to help protect against password-based attacks.
- Group Policy Objects (GPOs): GPOs allow administrators to control access to resources and enforce security policies, such as password policies and software installation rules.
- Security groups: Security groups can be used to control access to resources based on membership, making it easier to manage access to resources.
- Access controls: Active-Directory allows administrators to set access controls on resources, such as files, folders, and network shares, to control who can access the resources and what actions they can perform.
- Role-based access control (RBAC): Active-Directory includes RBAC, which allows administrators to assign roles to users and control access to resources based on those roles.
- Two-factor authentication: Active-Directory supports two-factor authentication, which requires users to provide a second form of authentication, such as a code sent to a phone or a security token, in addition to their password when accessing resources.
- Secure communication protocols: Active-Directory uses secure communication protocols such as LDAPS and Kerberos to protect the transmission of sensitive data between servers and clients.
- Auditing: Active-Directory includes auditing capabilities that allow administrators to track and log access to resources, helping to detect and prevent unauthorized access.
- Security principals: Active-Directory includes security principals, such as users, groups, and computers, that can be used to control access to resources.
3. What are the 3 main components of an Active Directory?
The three main components of an Active-Directory are:
- Domain: A domain is a logical grouping of resources, such as users, computers, and printers, that are managed as a unit. A domain has a unique name, such as example.com, and is used to identify the resources within the domain.
- Forest: A forest is a collection of one or more domains that share a common schema, global catalog, and security policies. A forest represents the highest level of organization in an Active-Directory environment.
- Domain controller: A domain controller is a server that stores a copy of the Active-Directory database and processes requests for authentication and authorization. Domain controllers are responsible for maintaining the security and integrity of the Active Directory database and ensuring that users and computers can access the resources they are authorized to use.
In addition to these three main components, Active Directory includes other components such as organizational units (OUs), group policy objects (GPOs), and security principals (such as users, groups, and computers). These components are used to organize and manage resources within the Active-Directory environment.
4. What are the risks to Active Directory?
There are several risks to Active Directory:
- Password attacks: Active Directory is vulnerable to password-based attacks, such as password cracking, password spraying, and pass-the-hash attacks. These attacks can allow attackers to gain unauthorized access to resources.
- Unsecured communication protocols: If communication protocols, such as LDAP or Kerberos, are not secured with encryption, sensitive data transmitted between servers and clients could be intercepted and compromised.
- Insufficient access controls: If access controls are not properly configured, users could have access to resources they should not have access to, increasing the risk of data leakage (learn more on data security) and unauthorized access.
- Lack of least privilege: If users are granted more access than they need to perform their job duties, it could increase the risk of unauthorized access and data breaches.
- Unsecured systems: If systems are not kept up to date with the latest security patches and are not adequately protected against malware and other threats, they could be compromised, leading to a breach of the Active-Directory environment.
- Lack of monitoring: If the Active Directory environment is not regularly monitored, it could be more difficult to detect and respond to security threats in a timely manner.
- Insider threats: Insider threats, such as malicious or careless employees, can pose a risk to the security of the Active-Directory environment.
- Physical security: The physical security of the Active-Directory environment, including servers and other infrastructure, is also a concern. If servers are not adequately protected, they could be compromised, leading to a breach of the Active Directory environment.
5. What are the 3 main advantages of Active Directory?
Here are three main advantages of Active Directory:
- Centralized management: Active-Directory allows administrators to manage users, computers, and other resources in a centralized manner, making it easier to control access to resources and enforce security policies.
- Single sign-on: Active Directory allows users to sign in once and access multiple resources, such as network shares, applications, and websites, without having to enter their credentials again. This can improve productivity and reduce the risk of errors due to incorrect passwords.
- Scalability: Active-Directory is designed to support large numbers of users and resources, making it suitable for use in enterprise environments. Active Directory also supports multiple domains and forests, allowing for greater flexibility and scalability.
6. Is Active Directory a security tool?
Active Directory offers a number of security capabilities that can be used to assist safeguard the network environment, but it is not a security technology in and of itself. Password policies, group policy objects (GPOs), security groups, access controls, role-based access control (RBAC), two-factor authentication, secure communication protocols, auditing, and security principles are some of these features.
By using these features, administrators can control access to resources, enforce security policies, and monitor activity in the Active Directory environment. This can help to reduce the risk of unauthorized access, data breaches (learn more on data security), and other security threats. However, Active-Directory is only one part of an overall security strategy and should be used in conjunction with other security measures, such as firewalls, antivirus software, and intrusion detection systems.




 You can copy the script from below too.
You can copy the script from below too.