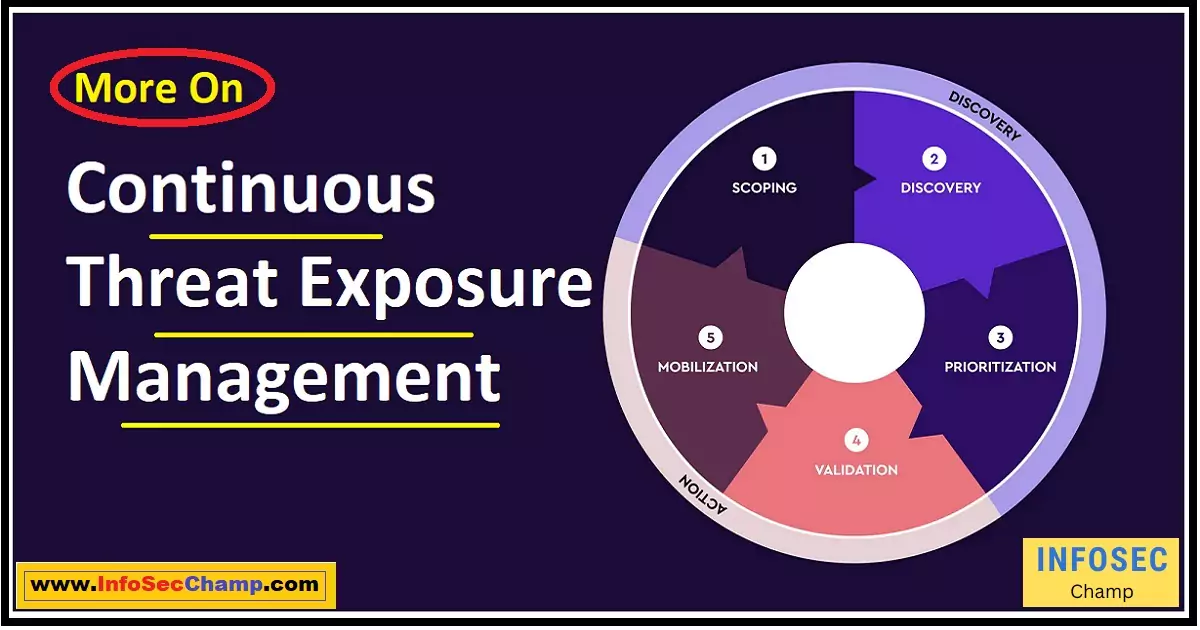
Cyber threats evolve at lightning speed, leaving organizations scrambling to keep up. The solution lies in continuous threat exposure management, an emerging approach that empowers businesses to stay steps ahead. This advanced technology enables real-time threat detection, accelerates incident response, and fortifies cyber defenses before attacks happen.
By continuously monitoring assets and attack surfaces, continuous threat exposure management exposes vulnerabilities and high-risk weak points across the entire IT environment. As soon as a new threat emerges, security teams are immediately notified and can take swift action to eliminate the risk. Breaches and cyber disasters are prevented before causing real damage.
Detect Threats in Real-Time
- Continuous threat exposure management employs advanced AI and ML algorithms to analyze massive threat feeds and detect anomalies in real time.
- Assets and attack surfaces are continuously monitored to identify vulnerabilities, misconfigurations, risky endpoints, etc.
- New threats are detected as soon as they emerge before causing any damage.
- Real-time alerting and visualization provide instant visibility allowing rapid response.
Respond Faster to Incidents
- Orchestration and automation capabilities allow continuous threat exposure management platforms to instantly initiate response procedures.
- Contextual threat intelligence aids in prioritizing the most critical incidents for the fastest response.
- Security teams collaborate efficiently with complete visibility of affected assets and risks.
- Response time can be reduced by 90% enabling containment of threats in minutes.
Fortify Defenses Proactively
- Identifying and mitigating vulnerabilities and misconfigurations before they are exploited fortifies defenses.
- Security posture is continually strengthened instead of reactive firefighting.
- Integrating with existing security solutions seals gaps and hardens the environment against attacks.
- Cyber resilience is achieved by fixing risks proactively.
How Continuous Threat Exposure Management Empowers Real-Time Threat Detection
- Continuous asset discovery and monitoring provide a real-time inventory of all assets and attack surfaces.
- Integrating threat intelligence enables identifying emerging threats as soon as they arise.
- Behavioral analytics spots anomalous activity indicating threats.
- AI and ML algorithms rapidly analyze massive feeds and data to detect threats in real time.
- Continuous visibility allows responding to threats early before the damage.
Accelerating Incident Response with Continuous Visibility of Assets and Attack Surfaces
- Real-time inventory of assets provides full contextual visibility speeding investigation.
- Critical assets can be isolated quickly during incidents to limit the damage.
- Orchestration capabilities accelerate containment procedures.
- Complete visibility of vulnerabilities and risks allows for precisely identifying and remediating root causes.
- Response playbooks can be executed faster with all relevant data available.
Fight Off Cyber Threats with Continuous Threat Exposure Management – The Ultimate Solution
- Detect threats in real time before attacks happen.
- Respond instantly to incidents minimizing damage.
- Fortify defenses proactively against emerging threats.
- Achieve end-to-end visibility of assets and risks.
- Hardened attack surfaces and security posture.
- Automates threat hunting, investigation, and response.
- Maximizes efficiency of security teams; less firefighting.
- Developed by cyber experts specifically to counter continuously evolving threats.
Conclusion:
Continuous threat exposure management is revolutionizing cybersecurity by enabling organizations to get ahead of threats before disasters strike. Its advanced capabilities empower real-time threat detection, accelerate response, and fortify defenses proactively.
Security teams can maximize efficiency and minimize business risk as they are empowered with continuous visibility of assets, risks, and threats. Adopting continuous threat exposure management solutions is imperative for achieving robust cyber resilience in today’s threat landscape. Organizations that embrace it now will gain a competitive edge and become industry leaders.

FAQs:
Q: What is continuous threat exposure management?
A: It is an emerging cybersecurity approach that provides real-time visibility of assets, vulnerabilities, and threats across the attack surface to detect and respond to threats before attacks occur.
Q: How does continuous threat exposure management work?
A: It continuously monitors assets, identifies risks, integrates threat intelligence, employs AI/ML for real-time threat detection, and accelerates response through orchestration and automation.
Q: What are the benefits of continuous threat exposure management?
A: Key benefits include real-time threat detection, rapid incident response, fortified defenses, and maximized efficiency of security teams.
Q: How is it different from traditional security solutions?
A: It is proactive, providing continuous visibility and helping strengthen defenses before attacks happen rather than just reacting post-breach.
Q: Is it difficult to implement continuous threat exposure management?
A: Leading solutions are designed to integrate easily into existing security stacks and provide rapid time-to-value.
Q: Does it require additional resources?
A: It aims to maximize existing security resources through automation and improved workflows.
Golden Quotes:
“The best defense is a good offense.” – Continuous threat exposure management takes cybersecurity defense to the next level.